As promised in the blog post for version 18.3.43, our development team is working diligently on the upcoming releases of PRTG. Since a few days ago, version 18.3.44 is available in the stable channel. In case you don't know about our new HTTP IoT Sensor yet, you can read more here. But let's have a closer look at the enhancements of the 18.3.44 release now.
The flow Sensors Are Up and Running Again!
Unfortunately, we had to inform you after the last release that in certain configurations, the NetFlow sensors weren't working reliably if you were using PRTG versions 18.3.43.2317 or 18.3.43.2323.
i If an installation was affected, the sensor types NetFlow V5, NetFlow V9, jFlow, sFlow, and IPFIX sensors did not receive data anymore after you updated to PRTG version 18.3.43. They turned gray and showed the message "No data received since x minutes."
We immediately set up a special "NetFlow Task Force" in the Development Team, who determined the cause of the problem. A location with incorrectly-initialized logging could shut down flow sensors through a chain of unfortunate circumstances.
In 18.3.44 the issue has been fixed. If you are having problems using the NetFlow sensors with your PRTG installation, we recommend updating to the current version.
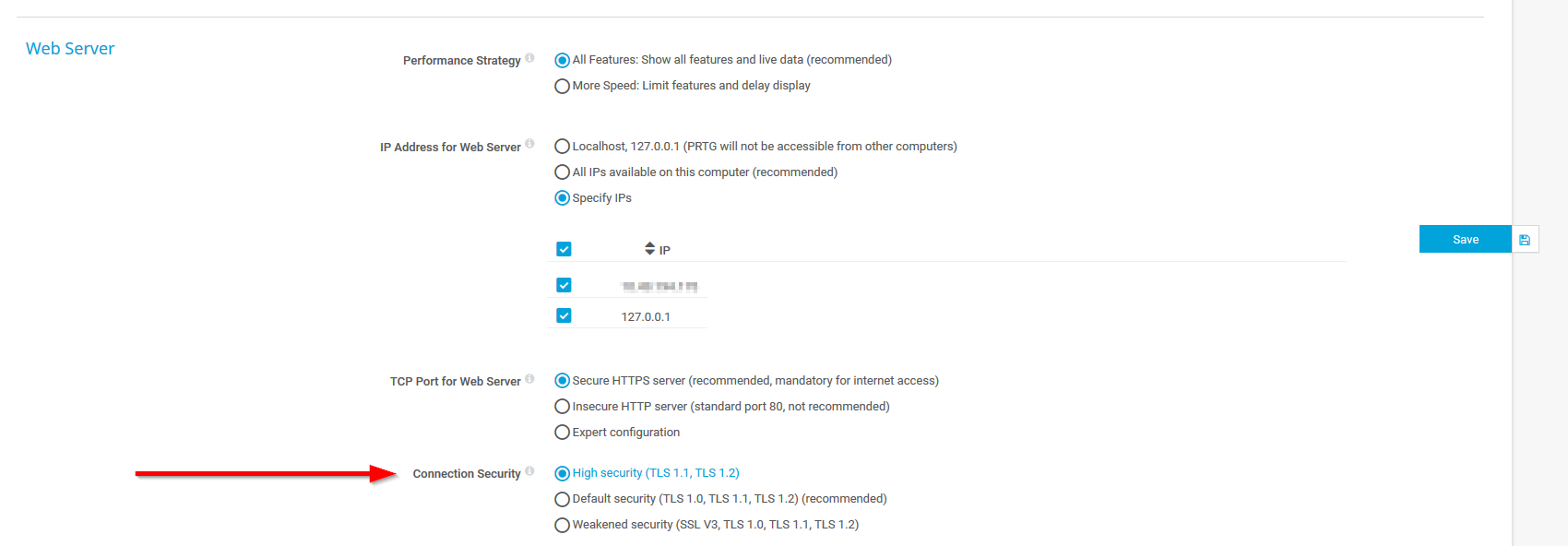
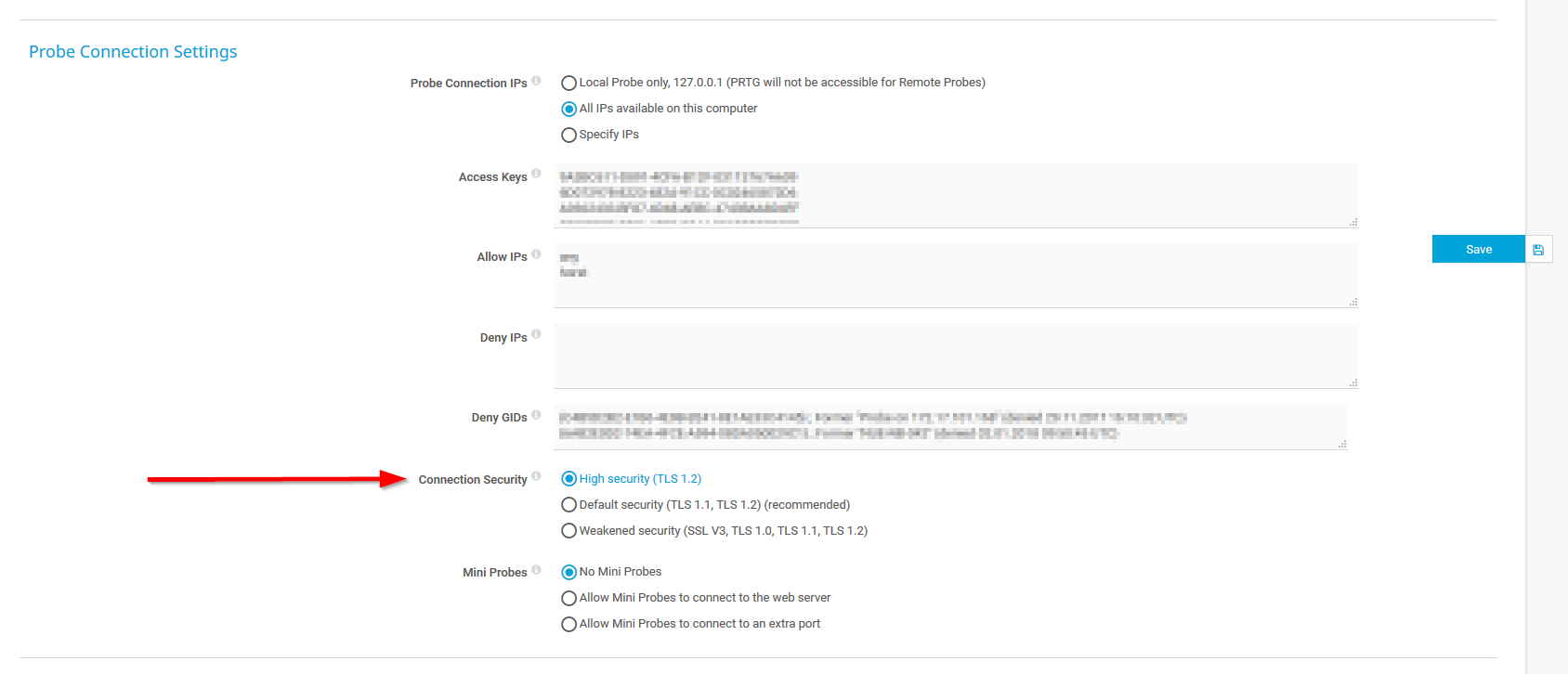
High Security Level for Web Server and Probe Connections
You are now able to define the security level for web server connections as well as for probe connections. You can disable TLS 1.0 and weak ciphers via the PRTG User Interface settings for web server connections and via the Core & Probes settings for probe connections.
With the high security setting, the web server only accepts connections from clients that support TLS 1.1 or TLS 1.2. Used suites must support authentication and 256-bit encryption or stronger (AES-GCM or AES-256), and forward secrecy (key exchange based on ECDH(E) or DH(E)). The default security setting additionally supports TLS 1.0 and 128-bit encryption. For more information see our Release Notes.
Improved Auto-Discovery Rescan
We improved the device rescan functionality of the auto-discovery. If you have selected the option Skip auto-discovery for known devices/IPs, PRTG will recognize more devices that were already discovered as known and skip the rescan. The improvement is especially useful if host names can be resolved to more than one IP address.
In addition to this, you can now start the auto-discovery with template on multiple devices at the same time via device lists and the multi-edit menu.
Core Health, Notification Triggers and More
We have provided the PRTG Core Health sensor with a new channel. The channel shows the time passed since the configuration file was last successfully saved. Sounds unimportant but is a quite helpful improvement in certain support cases. 😉
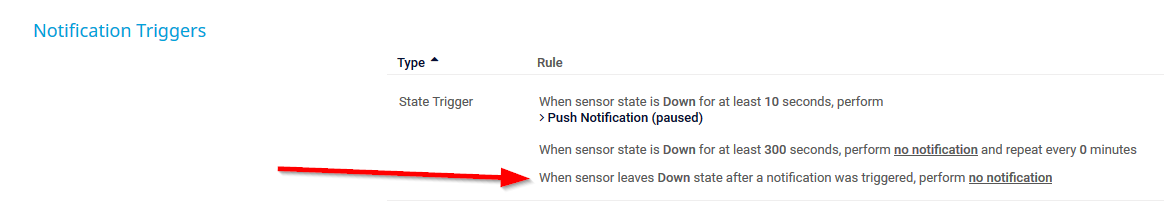
The "clear condition" for the State Trigger now denotes more clearly in which case the rule will apply because the status is explicitly mentioned.
We also improved performance for loading Active Directory groups on the setting pages of PRTG user groups, included some more improvements for the new logging framework (which is awesome by the way!) and fixed many more smaller and bigger issues, some noticeable, others behind the scenes! If you still don’t have enough, dive into our Release Notes page. After that, press Update and enjoy the current Release of PRTG! 😊
 Published by
Published by