Before we begin addressing the security and network monitoring implications of blocking Internet Control Message Protocol (ICMP) and Simple Network Management Protocol (SNMP), we must understand what they are and how they work.
Beyond Ping: Why ICMP is critical for network diagnostics
Ping is a network administration software diagnostic utility used to test the reachability of a host on an Internet Protocol (IP) network. The name traces its roots to submarine technology where active sonar is used to transmit a pulse of sound and listens for an echo to detect objects. Ping is part of the Internet Control Message Protocol (ICMP) suite.
The ping utility measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The utility operates by sending ICMP echo request packets to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. Ping is available for most devices and operating systems that have networking capability.
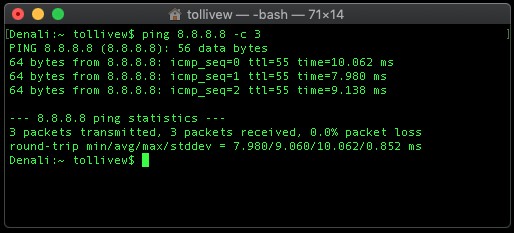
The command-line options of the ping utility and its output vary between implementations. Options may include the size of the payload, count of tests, limits for the number of network hops (TTL) that may be traversed and interval between the requests. Many systems provide a companion utility ping6, for testing on Internet Protocol version 6 (IPv6) networks, which implement ICMPv6.
How disabling ICMP affects your network monitoring tools
Ping is a central part of most network monitoring solutions on the market today. In network monitoring systems, the ping utility allows the Central Management Station (CMS) to quickly determine whether a monitored host or device is reachable. Other sensors configured for devices such as disk I/O, network bandwidth, etc. are often dependent on the ping sensor. If the ping sensor fails, the other sensors will likely be paused or taken offline to prevent alert storms.
Since ping has low overhead for both the CMS and network it is the preferred method of determining availability of monitored devices. Turning off ping typically involves re-architecting your network monitoring solution, increases administrative effort and complicates monitoring.
ICMP protocol: Designed for network control, not data transfer
Internet Control Message Protocol (ICMP), including ping, has no ports and is neither TCP nor UDP. ICMP is IP protocol 1 (see RFC792), TCP is IP protocol 6 (described in RFC793) and UDP is IP protocol 17 (see RFC768). Both UDP and TCP have ports, whereas ICMP has no ports, but does have types and codes.
ICMP differs from transport protocols such as TCP and UDP in that it is not used to exchange data between devices nor is it commonly used by end-user network applications. Because ICMP has no ports, it does not transport user data or information other than network statistics used for diagnostic and control purposes.
Security myths: Why disabling ICMP doesn't improve network security
Some network administrators disable ICMP and/or SNMP on network devices to improve security. Supporters of this position believe that it makes their network more secure by obscuring certain elements.
Disabling ping does not meaningfully increase security; it only makes troubleshooting and network monitoring much more difficult. If turning off ping increases network security, it only slightly slows down the most basic and unskilled cyber hacker. All other services such as HTTP(S), FTP, SMB, etc. are still running and likely discoverable.
By disabling SNMP, you significantly hamper your organizations ability to monitor infrastructure. Yes, other protocols like WMI, SOAP and the RESTful API are available, but they often incur much higher CPU utilization on the monitoring server and monitored devices. Additionally, not all aspects you wish to monitor may be available outside SNMP since it enjoys broad support.
Secure ICMP implementation: Best practices for safe network monitoring
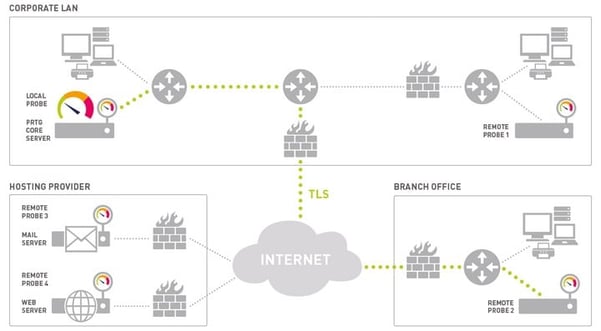
An alternative to globally disabling ping and SNMP is to whitelist network monitoring components such as servers and polling engines so only they receive responses from ICMP and SNMP packets. This can help prevent exposing certain aspects of your network infrastructure to unauthorized individuals while still reaping the benefits of network monitoring.
Here are four steps you can take to increase the security of your network while still allowing the use of ICMP and SNMP:
- Configure network and device firewalls to block ping traffic (reference types below) from unauthorized IP addresses and untrusted IP networks
- ICMP Type 0 – Echo Reply
- ICMP Type 8 – Echo Request
- ICMP Type 42 – Extended Echo Request
- ICMP Type 43 – Extended Echo Reply
- Configure network and device firewalls to block SNMP traffic (reference ports below) from unauthorized IP addresses and untrusted IP networks
- UDP port 161 – SNMP Agent
- UDP port 162 – SNMP Traps & Informs
- Specify the IP addresses of your SNMP polling engines and trap receivers (e.g. Paessler PRTG core server and/or remote probes) on your monitored devices. This limits the IP addresses the SNMP agent will exchange traffic with and provides another layer of protection if device firewalls are accidentally disabled or network firewalls fail. This is an example of an information security principle known as Defense-in-Depth.
- Be aware of Common Vulnerabilities and Exposures (CVE®) published for ICMP protocol stacks and SNMP agents on your monitored devices. It's always a good practice to keep device firmware, software and operating systems up to date to implement the latest security fixes which provides increased protection from attackers. CVEs are published by vendors in their release notes and available at https://cve.mitre.org.
Also, be aware that SNMP versions 1 and 2 do not include encryption and send data in the clear. Ensure the communication path between your polling engine and monitored device is secure. Alternatively, you may implement SNMP v3 which encrypts all communications between the polling engine and monitored device.

SNMP v1 or v2 should never be transmitted over the Internet unless though an encrypted tunnel. By default, all communications from PRTG remote probes to the core server are encrypted with Transport Layer Security (TLS) version 1.2.
The consequences of disabling ICMP: Network issues you'll face
ICMP is much more than echo request and echo reply (ping); it is also used for traceroute and time exceeded. Filtering out ICMP can lead to unintended consequences as Path MTU Discovery relies on receiving ICMP fragmentation needed packets. Path MTU Discovery (PMTUD) is a method used in computer networking for determining the maximum transmission unit (MTU) size on the network path between two hosts, with the goal of avoiding packet fragmentation. If Path MTU Discovery is unable to function, excessively large packets may be transmitted without fragmentation and will fail to reach the destination. This will lead to a retransmission loop with the same MTU only to be dropped again and again.
If you must filter ICMP, never filter ICMP destination unreachable or fragmentation needed packets; however, you may rate limit ICMP. Filtering ICMP will not lead to increased security, but it will make it more difficult to diagnose network issues and resolve configuration errors.
How PRTG leverages ICMP for comprehensive network monitoring
PRTG Network Monitor uses ICMP not just for basic ping tests, but as a foundation for sophisticated network monitoring:
- Enhanced ping sensors with configurable intervals down to 1 second for critical systems
- Advanced ICMP analysis for early detection of network degradation
- Multi-platform probe architecture with improved performance for ICMP monitoring
- Correlation of ICMP data with other network metrics for comprehensive visibility
- Visual traceroute tools to map network paths using ICMP
- Customizable alerts based on response times or packet loss thresholds
PRTG's next-generation database architecture enables faster query times and more efficient storage of ICMP monitoring data, allowing you to maintain historical performance records without excessive storage requirements.
PRTG's intuitive dashboard makes it easy to monitor ICMP metrics across your entire network.
Summary
Don't disable ping or filter ICMP unless you have advanced network knowledge and know exactly what you are doing. The disadvantages of disabling ICMP far outweigh the few benefits of doing so. Global security policy that disables ICMP or SNMP severely limits your ability to monitor your network. If turning off ping and/or SNMP are a core part of your information security strategy, your network won't be yours for long.
Numerous studies and users report the benefits of network monitoring: increased availability and organizations appreciating a proactive, rather than reactive approach from their system administrators. We cannot improve what we do not measure… or monitor.
Have you had problems after disabling ICMP and/or SNMP? What are your experiences? Just drop us a comment below!
 Published by
Published by 





.jpg)





