I still remember walking into that conference room at 3 AM, with executives pacing and developers pointing fingers. The e-commerce site was down, revenue was being lost by the minute, and nobody could figure out why. The network diagram taped to the wall was a sad joke - six months out of date and missing at least 30% of their infrastructure, including most of the AWS instances their dev team had been spinning up like there was no tomorrow. No wonder nobody could figure out what was happening.
Look, I've been in IT operations for over 15 years, and I don't throw around terms like "game-changer" lightly, but network topology mapping truly deserves that label. Those old Visio diagrams and handmade network maps we used to slave over? The ones where you'd spend weeks tracing cables, documenting IPs, and interviewing system owners, only to have everything change before you even finished? Complete waste of time.
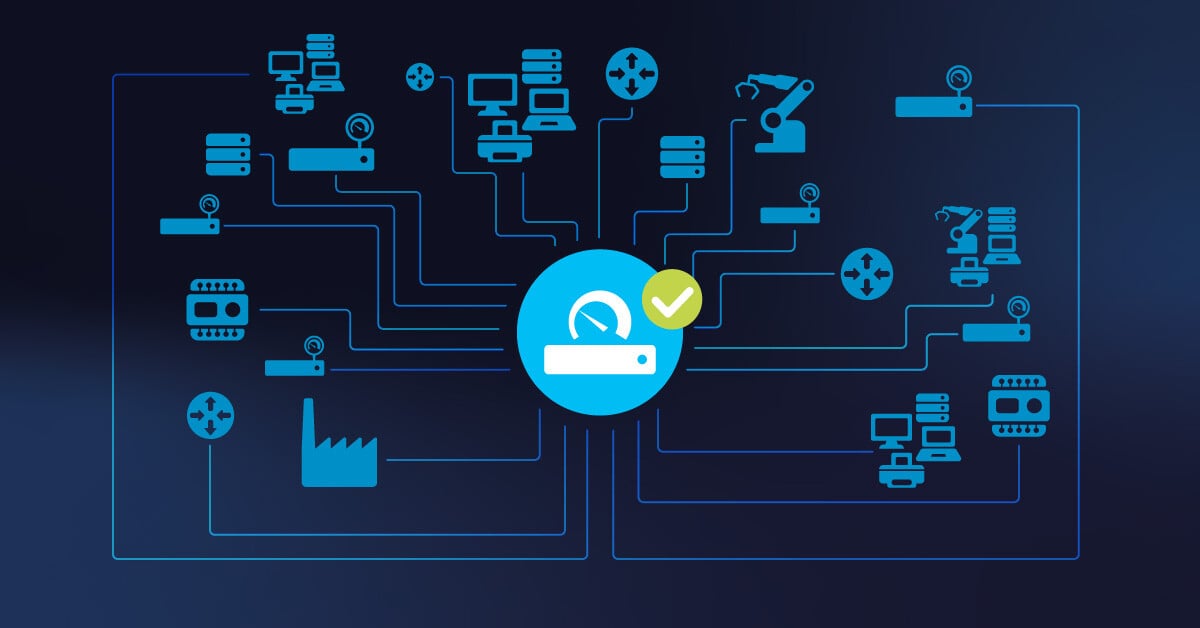
Today's network mapping tools actually do the hard work for you - they crawl through your environment (physical, virtual, cloud, whatever you've got) and show you what's really there, not what you think is there. They'll use SNMP for the network gear, WMI for the Windows servers, CDP for the Cisco equipment… basically whatever protocols they need to build a network diagram that actually matches reality. I still remember the first time I watched one of these tools discover a forgotten database server that had been running in a closet for years without patches or monitoring - simultaneously impressed by the technology and horrified by the security implications. And during those inevitable 2AM outages? Instead of the usual first hour of the blame game and arguing about what might be connected to what, you can actually see the dependencies and get straight to fixing the real problem.
Essential capabilities that define effective network topology mapping
After evaluating countless network mapping tools over the years, I've found there's a clear difference between the basic options and those that actually deliver real business value.
The tools worth investing in don't just rely on a single discovery protocol. Yes, SNMP works for many devices, but in real-world networks, it's never enough by itself. You need WMI to properly inventory those Windows servers, ICMP to verify basic connectivity, and CDP/LLDP to understand how your Cisco equipment is interconnected. I learned this lesson the hard way when a client's "complete" network map missed nearly 20% of their devices because their tool had limited discovery capabilities. When your mapping solution uses multiple methods, everything from core routers to virtual machines shows up in your diagram - which means fewer security blind spots and much faster troubleshooting when something inevitably breaks.
Visualization is another area where many tools fall short of what real IT teams need. Your network engineers require detailed interface-level data and bandwidth utilization metrics. Meanwhile, your IT managers need high-level dependency maps and performance trends. I've found that the best network topology mappers let each user customize their view without creating multiple, conflicting versions of reality. When paired with a thorough network assessment, these visualizations quickly highlight potential bottlenecks that might otherwise go unnoticed until they cause serious problems.
The most valuable capability, in my experience, is integration with monitoring systems. When your topology mapper connects with PRTG Network Monitor, those static diagrams become dynamic, actionable views of what's happening right now. I remember one particular outage where our team could immediately see not just which network segments were congested, but exactly which business services were being affected - allowing us to prioritize our response based on actual business impact instead of just technical metrics. This context-aware approach has saved countless hours during critical incidents.
How to map your network effectively with professional topology tools
I've implemented network topology mapping for organizations of all sizes, and here's what I've learned: you don't need to overcomplicate the process, but you do need a systematic approach. Start by getting crystal clear on your objectives. Are you trying to solve persistent network issues? Planning for growth? Strengthening security?
What you're trying to accomplish really shapes which mapping features you'll need. I worked with a regional healthcare system last year that made a classic mistake - they meticulously mapped their core infrastructure while completely overlooking the wireless network. Three months of mysterious afternoon outages later, we discovered their patient monitoring devices were competing with dozens of unauthorized wireless printers for bandwidth. Facepalm moment! A more comprehensive mapping approach would have caught this immediately and saved them weeks of frustration.
Don't rush the setup phase - I've seen this mistake too many times, and it always comes back to bite you. You need to thoughtfully configure your scanning parameters, which means identifying all the relevant IP ranges (including those odd subnets everyone forgets about), and tracking down credentials for everything. And I do mean everything: those obscure SNMP community strings for your routers, Windows admin accounts that haven't been used in months, Linux SSH keys stored on someone's laptop, and whatever special access your Cisco gear requires. Plus, if you're in manufacturing or utilities, how well do you know your OT network? Those systems are rarely as isolated as people think - a lesson many companies learn the hard way.
Once the initial discovery finishes, that's when things get interesting. The validation process almost always uncovers surprises - and not always good ones. A client in the financial sector thought they had tight control over their network until our mapping revealed three unauthorized access points hidden in ceiling tiles. Turned out an impatient department had created their own "solution" to poor WiFi coverage without telling IT. You can imagine the security implications. Their CISO nearly had a meltdown when we showed him.
The final hurdle - and where I see most organizations stumble - is integrating maps into everyday operations. Too often, companies invest in creating beautiful network diagrams that end up forgotten after the initial project. Your network maps should be living tools that support incident response, capacity planning, and compliance verification. Configure your mapping tool to display real-time metrics on the topology view, alert on unexpected changes, and create different perspectives for different stakeholders. Engineers need technical detail; executives need service impact views.
Transform your network management with comprehensive topology mapping
After 15+ years in network management, I've seen one thing consistently transform how IT teams operate: proper network topology mapping. Those Visio diagrams and open-source tools we all start with? They work until they don't - usually right when your network grows more complex with multiple subnets and cloud environments in the mix.
What separates struggling IT departments from high-performing ones is their visibility tools. The best mapping solutions deliver true end-to-end observability that makes a real difference: I've seen teams reduce costly downtime by catching bandwidth bottlenecks before they affect users, strengthen security by finding vulnerabilities that scanners missed in critical network segments, and simplify compliance with requirements like PCI. The technical difference comes down to comprehensive discovery.
By combining multiple protocols (SNMP for network gear, WMI for Windows systems, ICMP for basic connectivity, and CDP for Cisco equipment), these tools create a complete picture of your infrastructure - from core routers to virtual machines to Linux servers. This isn't just about documentation - it's about shifting from reactive firefighting to actually managing your environment. Teams that make this transition can finally plan capacity based on real data, address network issues before users notice them, and build IT infrastructure that supports growth rather than constrains it.
Good network monitoring doesn't just show you what you have today - it helps you build what you need tomorrow. Ready to see what proper visibility could do for your organization? get a free trial of PRTG Network Monitor and experience the difference for yourself.
Frequently Asked Questions
What's the real difference between a network topology mapper and basic monitoring tools?
This difference isn't just theoretical - it becomes painfully obvious during network outages. Here's a real example from last quarter: A client's customer database went down during month-end processing (of course it did, right?). Their monitoring dashboard showed the database server with high latency, so naturally, the database team got the 2AM call. After an hour of fruitless troubleshooting and lots of finger-pointing, someone finally pulled up their network diagram and spotted the actual problem - a core switch three hops away was dropping packets and affecting multiple systems. Without that visual context, they were just chasing symptoms. I've seen this scenario play out countless times, and it always ends the same way - the team with good network visualization finds the root cause faster and gets to go back to sleep sooner.
How frequently should I actually update my network topology maps?
It really depends on your environment's rate of change. If you've got a fairly stable network infrastructure without much churn, monthly updates might be sufficient. But let's be honest - that's increasingly rare these days. Most organizations I work with are constantly adding cloud resources, spinning up VMs, or making config changes. For these environments, weekly updates are the minimum, and some of my clients in tech or financial services run daily discovery scans. I learned this lesson the hard way after spending half a day troubleshooting what turned out to be a new VLAN someone had implemented two weeks earlier that wasn't in our documentation. Not my finest moment.
Most teams I consult with just schedule their network discovery scans to run overnight when nobody's around to complain about the extra traffic. That way their documentation stays current without affecting business operations.
Learn how regular network discovery strengthens your cybersecurity risk assessment by identifying unauthorized network devices before they become security incidents.
Can network topology mapping tools really discover devices across both IT and OT networks?
I was working with a 300-bed hospital in the Midwest last year that was absolutely convinced their networks were properly segmented. Their IT director kept assuring me their medical device network was completely isolated from their main IT systems - they'd even passed their last audit with flying colors. When we ran our first comprehensive mapping scan, there was this awkward silence in the room as we found not one, but seven unauthorized connections between their clinical systems and the general network. Turns out their biomedical vendor had installed wireless bridges to 'improve support efficiency.' Their CISO actually had to leave the room for a few minutes to compose himself - I thought he might quit on the spot. They ended up doing an emergency remediation project that weekend and completely revising their vendor access policies. Last I heard, they're still doing quarterly scans just to be sure.
Explore understanding MQTT architecture: a deep dive to see how modern monitoring tools can bring visibility to your industrial systems and IoT devices.
 Published by
Published by