It's almost December and yet 2014 doesn't seem to leave any room for peace and quiet—at least not for system administrators. Even in the year's final quarter there seems to be no break from new headlines about security vulnerabilities: 2014 will definitely be one of those years for everyone in IT to remember.
Besides the well-known Heartbleed Bug, which was even prominently discussed in mainstream media, there were several other issues and security breaches that influenced users and admins alike in one way or another. Take, for example, the eBay breach, which resulted in millions of stolen passwords, addresses and other user data. Or the dawn of a new aggressive form of ransom attacks, which are often directed at popular web services like, for example, the RSS reader Feedly. It seems that cybercriminals are upping their game and are getting more creative by the minute. As a software developer it is our responsibility to do everything in our power to be always at least one step ahead and provide a safe and sound user experience for our customers.
That's why, over the last few months, we at Paessler have undertaken several efforts to implement a lot of security enhancements in PRTG versions 14.x.11 and 14.x.12 which will let you monitor your IT infrastructure with an even better feeling of safety than ever before. We have massively upgraded the encryption security of the PRTG web server to make the usage of PRTG even more secure and implemented changes to the behavior of PRTG in order to prevent potential attacks on your personal data. PRTG has access to sensitive data in your network so it is our duty to keep everything as safe as possible!
Taking Encryption Security to the Next Level
The current PRTG release contains massive changes for the way we use SSL inside PRTG to provide the most secure PRTG you have ever seen. We upgraded PRTG's OpenSSL libraries to the 1.0.1 branch and use elliptic curve cryptography for much safer connections and data, and we implemented support for the protocols TLS 1.1 and TLS 1.2.
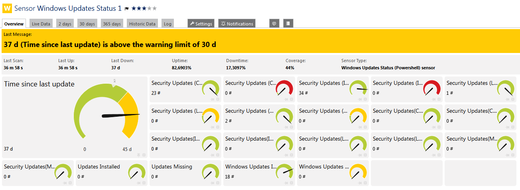
PRTG uses SSL for connections of the web server and clients (for example, web browser, Enterprise Console, mobile apps, API), for core to probe connections and vice versa, as well as for core to core connections within a cluster. With the latest enhancements of PRTG's SSL usage, we ensure the most secure platform that is possible and reasonable for PRTG at the moment. In fact, TLS 1.2 with "Forward Secrecy" is now mandatory for PRTG internal connections!
For example, this upgrade helps prevent man-in-the-middle (MITM) attacks where traffic of clients and servers could be decrypted and modified, remote DoS attacks, data injections, and includes other security fixes of OpenSSL as well. If you want to know more details about OpenSSL security in this version, please have a look at the OpenSSL Security Advisory notes from June 2014.
We also said that PRTG will now only accept the most secure ciphers for SSL connections. These ciphers have to allow "Perfect Forward Secrecy" and TLS 1.2 to ensure that a session key which is derived from a set of long-term keys cannot be compromised if one of the long-term keys is compromised in the future. To support systems which cannot handle elliptic curve cryptgraphy, PRTG generates a unique Diffie-Hellman key for each installation. This means that even if somebody wire taps your communication with your PRTG server and gets access to your private keys at some later point in time, this person would not be able to decrypt old data easily. Modern web browsers natively support this functionality.
Furthermore, most sensor types which offer the option to use secure SSL connections use now the safest SSL/cipher combination accepted, trying from highest to lower security as fallback, just as web browsers do. For your convenience, you do not have to configure the encryption setting for each sensor individually, but the sensors automatically use the matching security protocol version.
Please note that if you still use very old browser versions (for example, Internet Explorer 6 or 7, browsers on Windows XP, some default browsers on Android systems), you will not be able to connect to PRTG's web interface anymore. For this concern, we provide an option in the User Interface settings where you can switch to a lower security level. Only do so if you still need the login possibility with clients which use older security mechanisms (this could also apply to PRTG Mini Probe connections, for example). However, we strongly recommend you to leave the high security setting untouched and rather try updating your clients—it's for your own safety! Also note that old-fashioned browsers are not officially supported by PRTG.
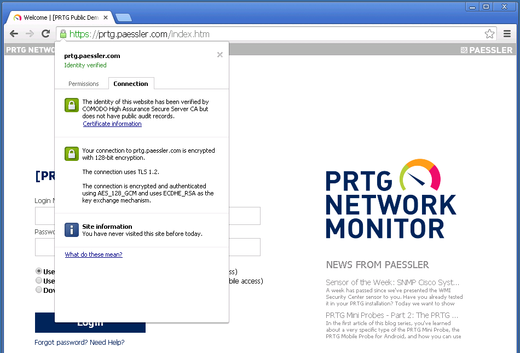
Another security improvement regarding encryption is the new default certificate for PRTG, now with RSA 2048 bits. It overwrites automatically the previous default certificate with the update to PRTG 14.x.11. The new default certificate secures PRTG connections much better and will protect your installation against potential attacks. Of course, if you use your own custom certificate, this will not be changed.
Please see this article in our Knowledge Base for an overview about all side effect of these security improvements and how they might affect you.
Security Enhancements in the Behavior of PRTG
We did not only improve the encryption methods of PRTG connections but also included some security tweaks into the operating processes of PRTG, including some minor security options and improvements. These include:
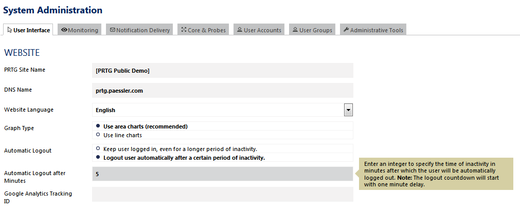
- Authentication: When you work on administrative pages in the PRTG web interface (i.e., Account Settings and System Administration), you will now have to re-authenticate yourself before you can continue your task if the last credential based login was more than 15 minutes ago. Furthermore, the PRTG administrator can define a time span of inactivity after which the current user will be automatically logged out from PRTG and redirected to the login page. Both mechanisms help prevent unauthorized access to PRTG and secure the web interface against potential phishing attacks.
- Disabling login auto-complete: You can now disable browser form auto-complete on the login page for the Login Name and Password fields. Switch on this security enhancement if you want to be on an even safer side via a registry key option. Find detailed instructions in our Knowledge Base.
- Denying frames: We have also implemented an additional protection mechanism against clickjacking attacks. With another registry key option, you are able to deny the loading of PRTG web pages in frame elements. See our Knowledge Base for details. Caution: This option also denies loading PRTG Maps!
- Remove passwords: If you use the support bundle in PRTG to contact us, all encrypted passwords will be removed from the config.dat file before you send it to our support team. This functionality will keep your passwords safe from someone else's eyes. Of course, the passwords used to be encrypted before so that they were not publicly available and only the Paessler tech support had access to them.
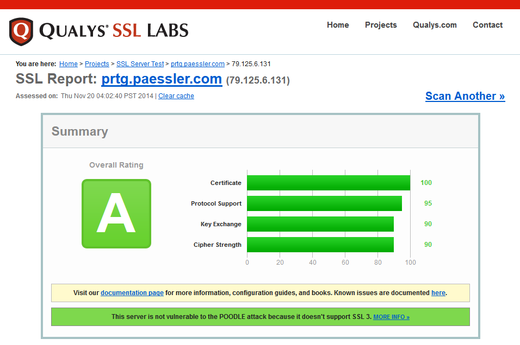
We put a lot of effort into providing you the most secure network monitoring solution possible. Besides some minor (optional) security enhancements, we focus our attention especially on secure PRTG connections. And this effort results in an overall SSL security rating of A on Qualys SSL Labs. Of course, we will continue keep a close eye on PRTG's security in future!
 Published by
Published by