Following up my first blog article, Secure communication within Paessler PRTG, which covered how to set up security measures in PRTG, this article I will explain the various layers of security PRTG implements. These layers reduce the risk of unauthorized access to PRTG, which can jeopardize the underlying operating system (OS). In this article, I will also share our recommendations on how to securely handle the PRTG configuration file.
Overload protection
The first feature that PRTG embeds is the so-called overload protection. This feature is a built-in mechanism to fight brute-force attacks. More specifically, upon experiencing multiple false login attempts, PRTG increases the time required for the next login attempt considerably. You can read more about this feature in the Knowledge Base: What is overload protection?
Enhanced security with automatic log out
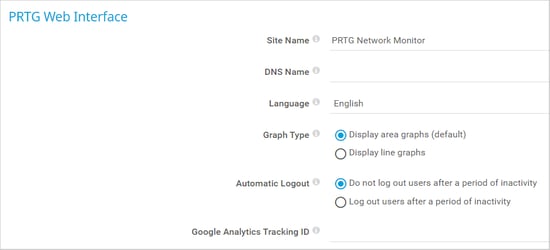
PRTG also allows users to set an automatic log out option (Setup | System Administration | User Interface | PRTG Web Interface). Enabling this feature requires users or administrators to log in again after a period of inactivity.
As a result, even forgotten unlocked sessions are locked, reducing the possibility of accidental or malicious insider threat attacks. For more information on how to set up this feature, see the PRTG Manual: User Interface.
Preventing malicious code execution
While features like the one mentioned above help reduce the risk of a successful infiltration into PRTG, another layer of security exists for cases where a malicious actor has already gained access to a PRTG instance. To minimize the potential for damage, PRTG is set up in such way that it restricts the possibility of being used to execute malicious code. This is possible because changes made to certain sensors (e.g. custom sensors) do not occur within PRTG.
Thus, even though someone malicious might have access to a Paessler PRTG instance, they are not able to utilize the UI to create a new custom sensor using a malicious script or alter an existing one and execute it. Instead, OS system administrators need to edit or create the script directly and place it in a specific location that PRTG can read from.
In default installations, access to this location requires high privileged permissions in the server itself.
You can read more about this feature in the Knowledge Base: Why do I have to store SQL sensor queries and custom scripts in files on the probe computer?
Secure configuration file
Finally, there is an additional layer of security with regards to the PRTG configuration file. Paessler PRTG stores the entire PRTG configuration – sensors, devices, credentials, etc. - in a configuration file. Not only is this configuration file stored in a location that only a user with administrator permissions can access by default, PRTG also encrypts all secrets or passwords using AES-256; no secrets can be found in plain text in the configuration file.
PRTG decrypts these secrets as needed during runtime. By doing so, we reduce the risk of accidentally leaking confidential information. Additionally, PRTG is designed in such way that if a customer shares this file through the support bundle, the secrets are automatically removed. Our support team can only see the configuration; we cannot see any associated secrets. The same security measures are applied to every automatic backup of the configuration file.
Of course, as a general recommendation for all files, but especially for the configuration file and any automatic backups, administrators should not depend solely on PRTG and their OS for security. Rather, administrators should take the necessary steps to ensure that the security and access control for the configuration file is maintained during transit, deployment, and storage (e.g. backups).
We highly recommend that you read the section in the PRTG Manual where we provide specific details about the existence of the configuration file, its automatically created backups, and recommendations on how to handle the file appropriately in different scenarios.
Get in touch with us
As shown with the security features mentioned above, PRTG implements security features in layers, achieving in-depth security. As a result, even if one security measure fails, other security features are in place to help reduce the risk of a successful attack intended to leak data, execute unwanted code, or even further damage the underlying OS.
However, security is a never-ending story and thus we encourage everyone to contact us at security@paessler.com to report potential security issues or concerns.
 Published by
Published by