Palo Alto Networks based in Santa Clara, California provides their 45,000+ customers in 150+ countries a "Next-Generation Security Platform" through their firewalls and security management tools. Palo Alto Networks is the security company maintaining trust in the digital age by helping organizations prevent cyber breaches.
Palo Alto's cybersecurity expertise and security platform allows customers to confidently pursue a digital-first strategy and embark on new technology initiatives, such as cloud and mobility. Thousands of administrators across every industry are utilizing the Palo Alto platform to control and protect their critical systems and most valued data assets.

It's great to have an industry leading security appliances in place but what if the device or network connected to it has an issue? How do you maintain visibility to your Palo Alto devices along with the rest of your network simultaneously? How can you monitor your Palo Alto to ensure they are performing adequately and providing the level of protection you expect? Palo Alto devices provide administrators various ways of collecting data and points of integration for network telemetry and reporting.

Palo Alto devices are Linux based and support SNMP v2c and v3 while providing the SNMP mibs for polling specific aspects of these devices.
iSNMP stands for Simple Network Monitoring Protocol. Its usefulness in network administration comes from the fact that it allows information to be collected about network-connected devices in a standardized way across a large variety of hardware and software types. SNMP is a protocol for management information transfer in networks, for use in LANs especially, depending on the chosen version. Read more ...
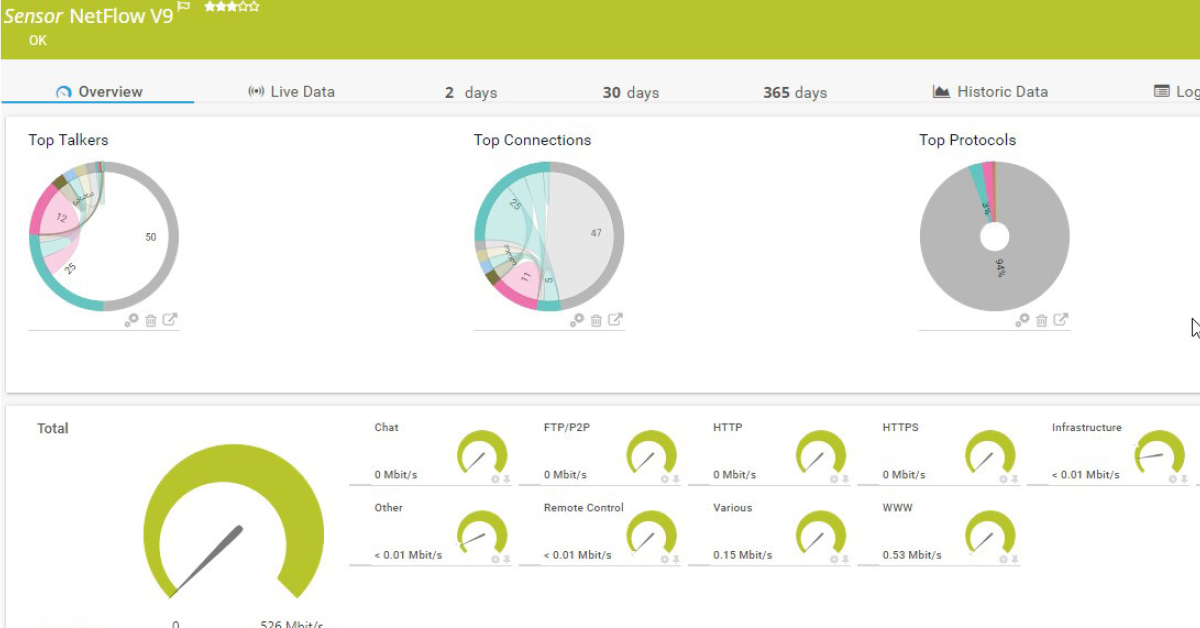
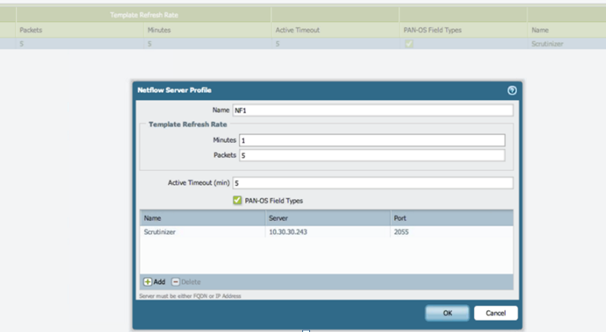
Palo Alto also supports syslog messages and SNMP trap forwarding to an SNMP management station or syslog receiver. Along with these monitoring components include the ability to capture Netflow V9 packets for an aggregate view of bandwidth consumption by device, connection and protocol. SNMP access allows administrators to monitor uptime, health and interface traffic.
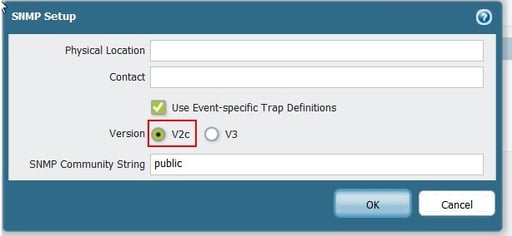
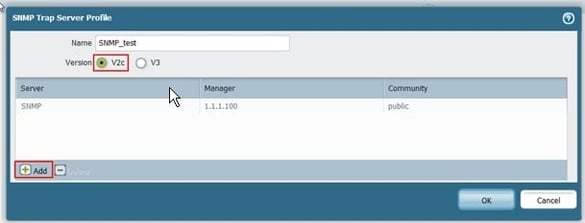
SNMP Configuration
For details on how to configure SNMPv2 on the Palo Alto Networks firewall, please see this article.
Does PRTG Work With Palo Alto?
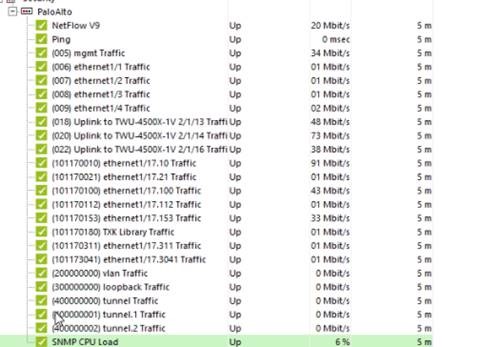
Of course! For those of you who are new or maybe not so new to PRTG Network Monitor and Palo Alto, you can obtain device status and performance with out of the box sensors from PRTG for monitoring each of your Palo Alto virtual or physical firewall appliances. SNMP is available to monitor Uptime, CPU load and interface traffic. In addition, the Palo Alto SNMP mibs are available to create custom sensors for other important metrics through the PRTG MIB Importer.
If you look at this GitHub page, you'll find a project, which contains all the files necessary to integrate the PaloAlto PanOS into PRTG for auto discovery and sensor creation.
Standard Sensors
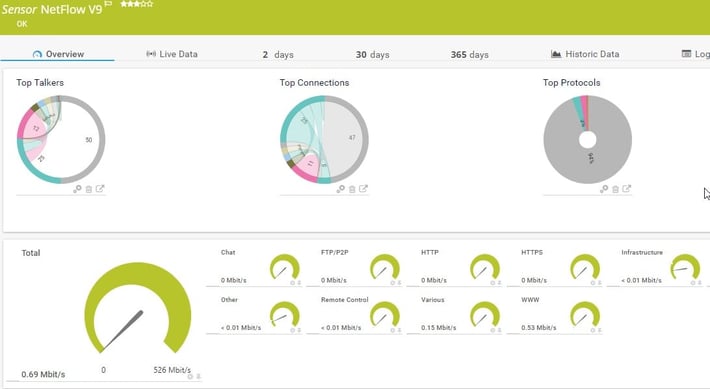
Netflow Configuration
REST API Anyone?
One of our PRTG users wrote a PowerShell script for monitoring an IPSec VPN Tunnel via the rest API on a Palo Alto.
This is just another example of the customization and flexibility of PRTG to capture and monitor devices and services in countless ways. IT professionals need to collect as much data from their environment as possible to ensure everything is working properly.
Are you using PRTG to monitor your Palo Alto devices? What other ways have you found to monitor and track security related issues in your environment? Tell us below!
 Published by
Published by