Industroyer, NotPetya, EKANS, Triton, LockerGoga. If those five words just sent a chill down your spine, chances are you work in the industrial control sector. For decades the OT world relied on “security through obscurity” to guarantee its safety – it’s difficult to attack a network that you can’t connect to. Unfortunately, for most companies, completely isolating their ICS environments from the outside world is no longer an option. Increased need for IT/OT convergence, remote access support demands from equipment vendors, and the need to collect, analyze and store sensor data from IIoT applications all mean that industrial networks are increasingly connected to the outside world. Therefore, they are vulnerable to attack.
The IT realm has been managing these risks for a long time and there are countless security tools for identifying and mitigating threats to IT networks. However, the unique requirements of many OT environments mean that traditional IT security tools like IDS/IPS or endpoint security scanners simply cannot be deployed.
In many OT environments, stability and consistency are of paramount importance. OT networks have been described as “deterministic, finite state machines” – systems that will react in a known, predictable way to any given change. Where enforced, this absolute need for stability takes priority over everything else, including keeping firmware and software updated – unpatched devices are vulnerable devices. It’s also not uncommon for OT networks to prohibit any third-party application from introducing any traffic onto the network. This can mean unidirectional security gateways or “data diodes” are mandatory requirements for installing software in the OT space.
Finally, add in the huge list of specialized, or even proprietary, protocols and it’s easy to see why IT centric security tools are unsuitable for use in OT environments. So, what’s the answer?
Special circumstances demand special solutions
With OT’s many unique requirements, purpose-designed solutions are needed. One such tool is Rhebo Industrial Protector (RIP) – an application specifically designed to detect anomalous or malicious activity in the OT network, whether the threat originates from outside or inside the organization. RIP is built upon an innovative deep packet inspection “anomaly detection engine” that allows OT engineers and NOC / SOC analysts to:
- Gain visibility of the ICS network
- Detect malicious or anomalous activity
- Increase plant availability
- Protect data
- Facilitate OT/IT convergence
- Undertake a forensic analysis of attacks.
Available as either a hardware appliance or a VM image, RIP’s architecture is very similar to that of an award-winning network management solution, that we all know and love. The system consists of two main components – the “Controller” (think, PRTG Core Server) and, optionally, one or more “Sensors” (analogous to our Remote Probes). Like PRTG’s “Local Probe”, the Controller includes a built in Sensor. So, for a small or simple network, there is no need to deploy additional sensors, the Controller can collect the data directly. But, for more complex environments, additional Sensors can be deployed. Sensors are responsible for gathering traffic from their local network segments and passing it back to the Controller to process. Sensors are also available as hardware or virtual appliances. There is also a version available that runs in a container on an INSYS icom Smart Edge Gateway.
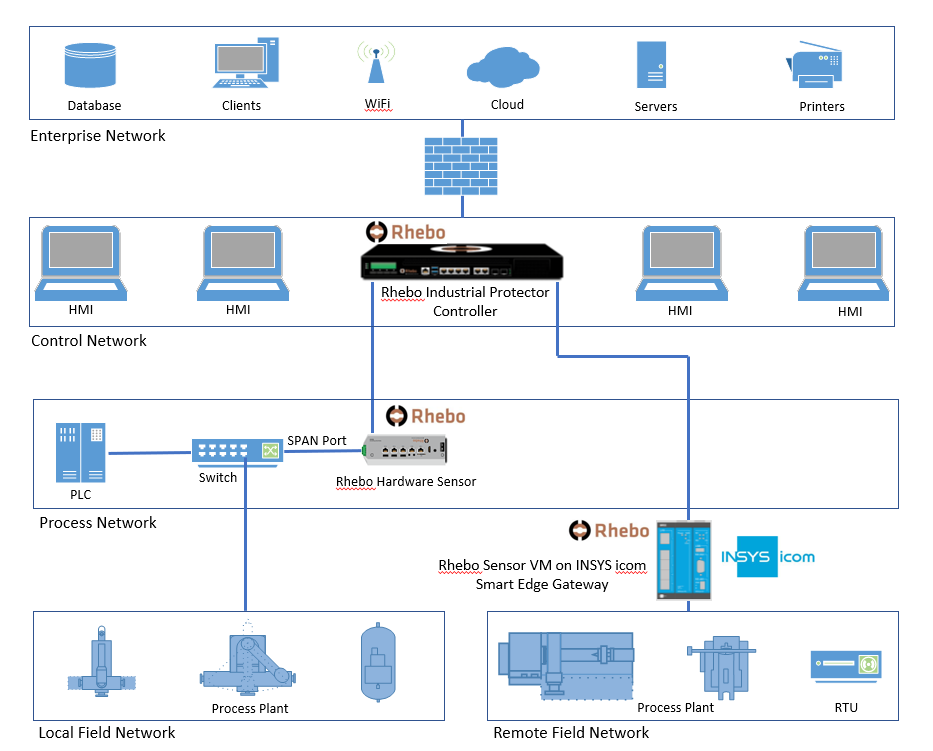
RIP is an entirely passive solution, that introduces no traffic onto the monitored network. Instead, it collects data through the use of SPAN / Mirror switch ports, or hardware taps. The system then uses Deep Packet Inspection (DPI) techniques to dissect and analyze the received traffic. Both the packet headers and the payload are examined, allowing RIP to understand where the packet originated, where it’s going, and what it’s intended to do when it gets there.
Out of the box, RIP recognizes over 120 protocols, including both OT specific protocols such as Modbus, S7/S7+ and DNP3; as well as common IT protocols such as DNS, SSH and RDP. Additionally, custom protocols can be defined and included in the traffic analysis. Cybersecurity tools have traditionally relied on “whitelists” and “blacklists” to identify suspicious traffic. But this only works for known, previously seen activity. Instead, Industrial Protector leverages Rhebo’s expert knowledge of OT protocols to understand the payloads contained in collected network traffic. This allows the system to detect any dangerous or anomalous data contained in that traffic. This could include:
- Newly connected devices
- Previously unknown data types
- Known malware behavior
- New inter-device connections
- Unexpected PLC programming
- Changes to command structure
Analyzed traffic is used to construct a “network map” to illustrate detected devices and the connections between them:
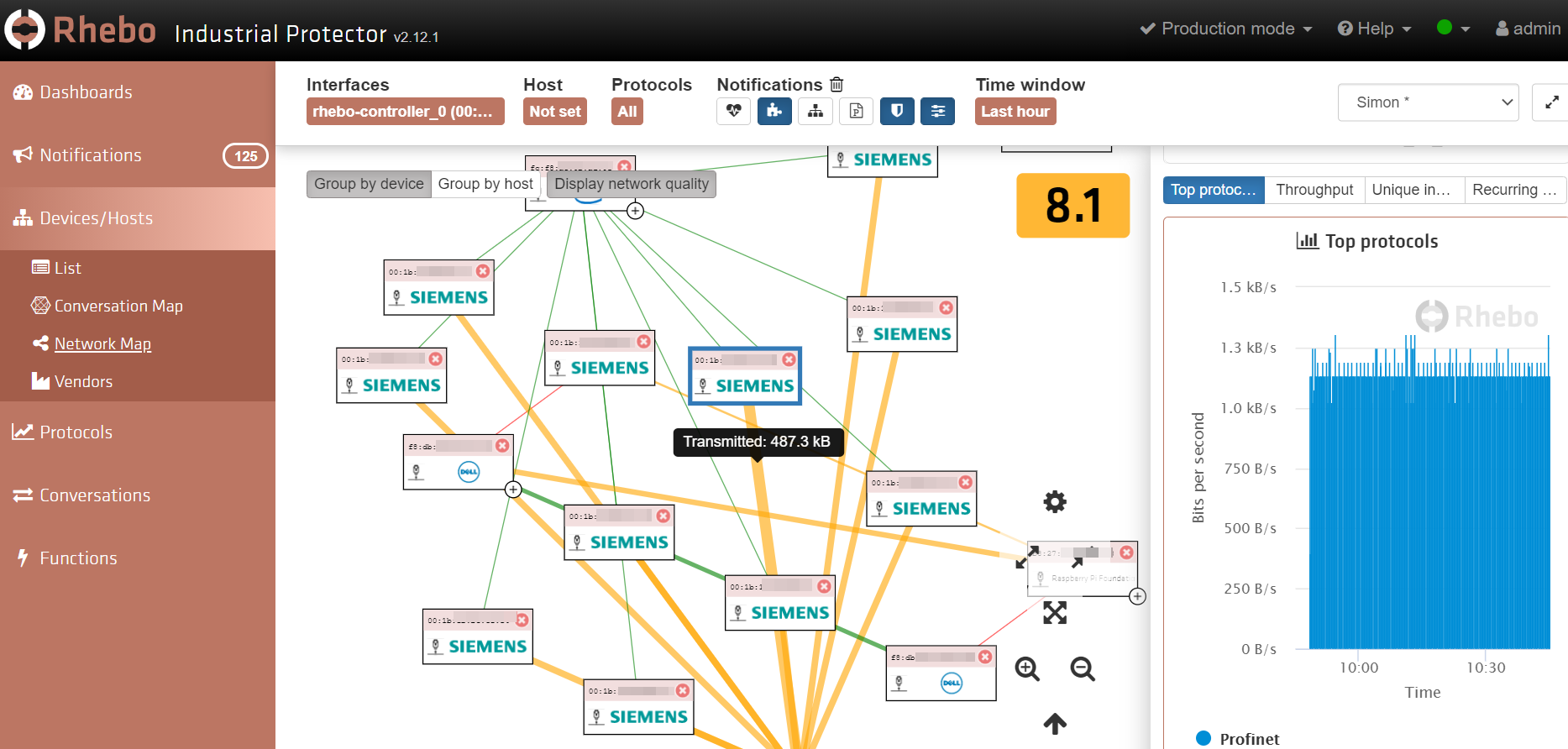
Administrators can click on the links to check bandwidth usage and selecting devices shows detailed information about the conversation.
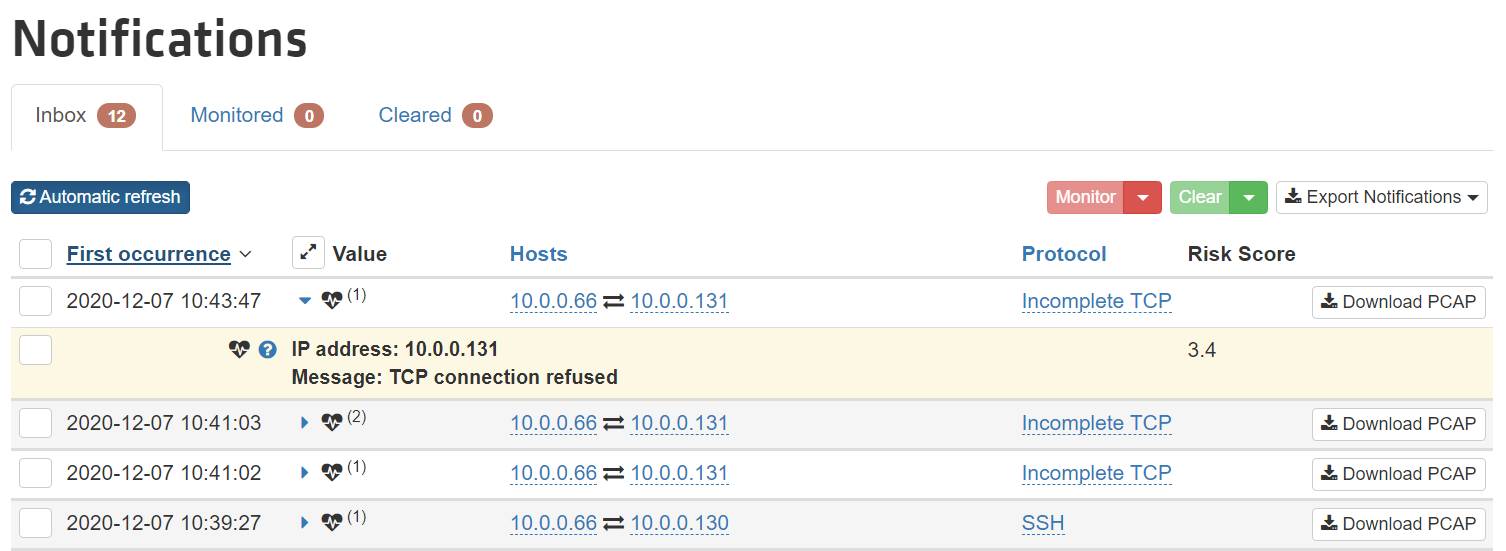
Any anomalous behavior detected will trigger a “notification” and because every OT environment is different, these parameters can be tuned, to eliminate false positives. Notifications can be filtered and displayed according to type – newly detected connections, new protocols, security events, and so on.
In addition, RIP will also analyze discovered devices for any known CVE vulnerabilities pertaining to the installed software / firmware versions. CVE intelligence is constantly updated so administrators will always be aware of newly discovered vulnerabilities:
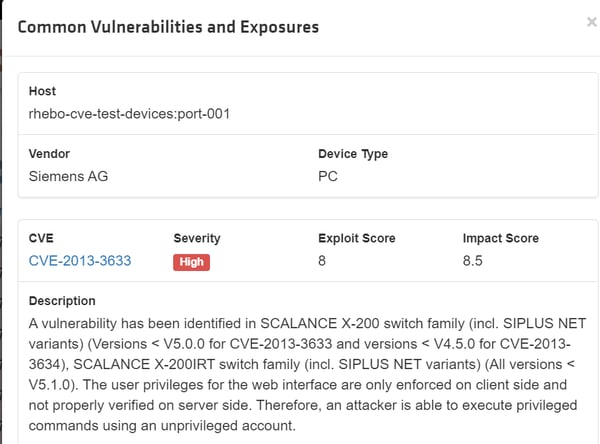
Any activity or event, in violation of configured thresholds, can be used to trigger alerts by email, Syslog or Trap.
Much of the data collected by RIP is used to determine a “Network Quality Score”. This is a simple indicator of the overall “health” of the monitored environment and is based on a scale of 1 – 10. Network events such as checksum errors or dropped packets will reduce the score, which allows administrators to keep track of the state of their environments. It also allows them to quantify the performance impact of any changes made to the network.
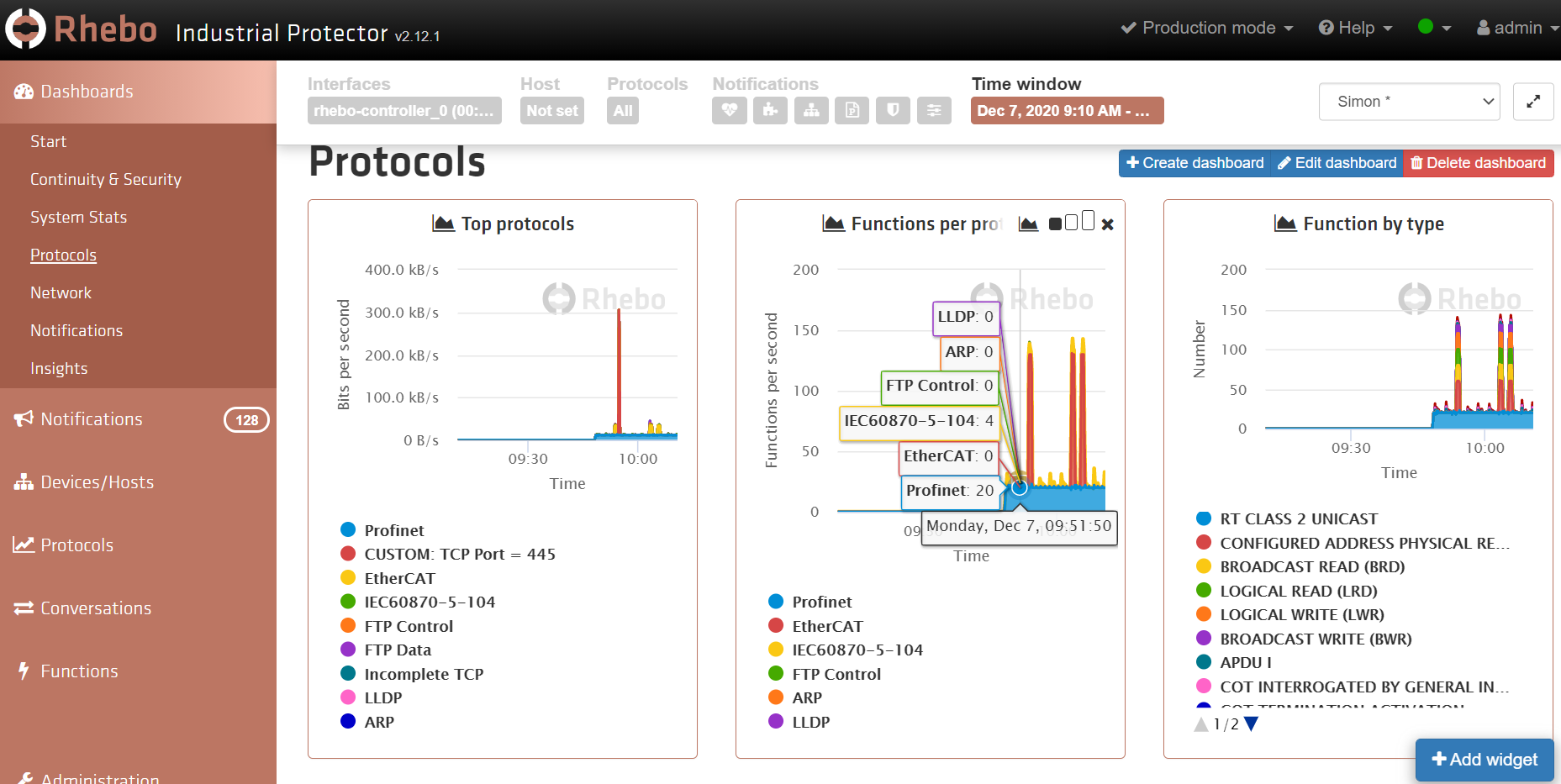
Finally, all of the collected information can be displayed on dashboards. These can be customized to suit the needs of different types of user. For example, OT Engineers are likely to be interested in asset and protocol information:
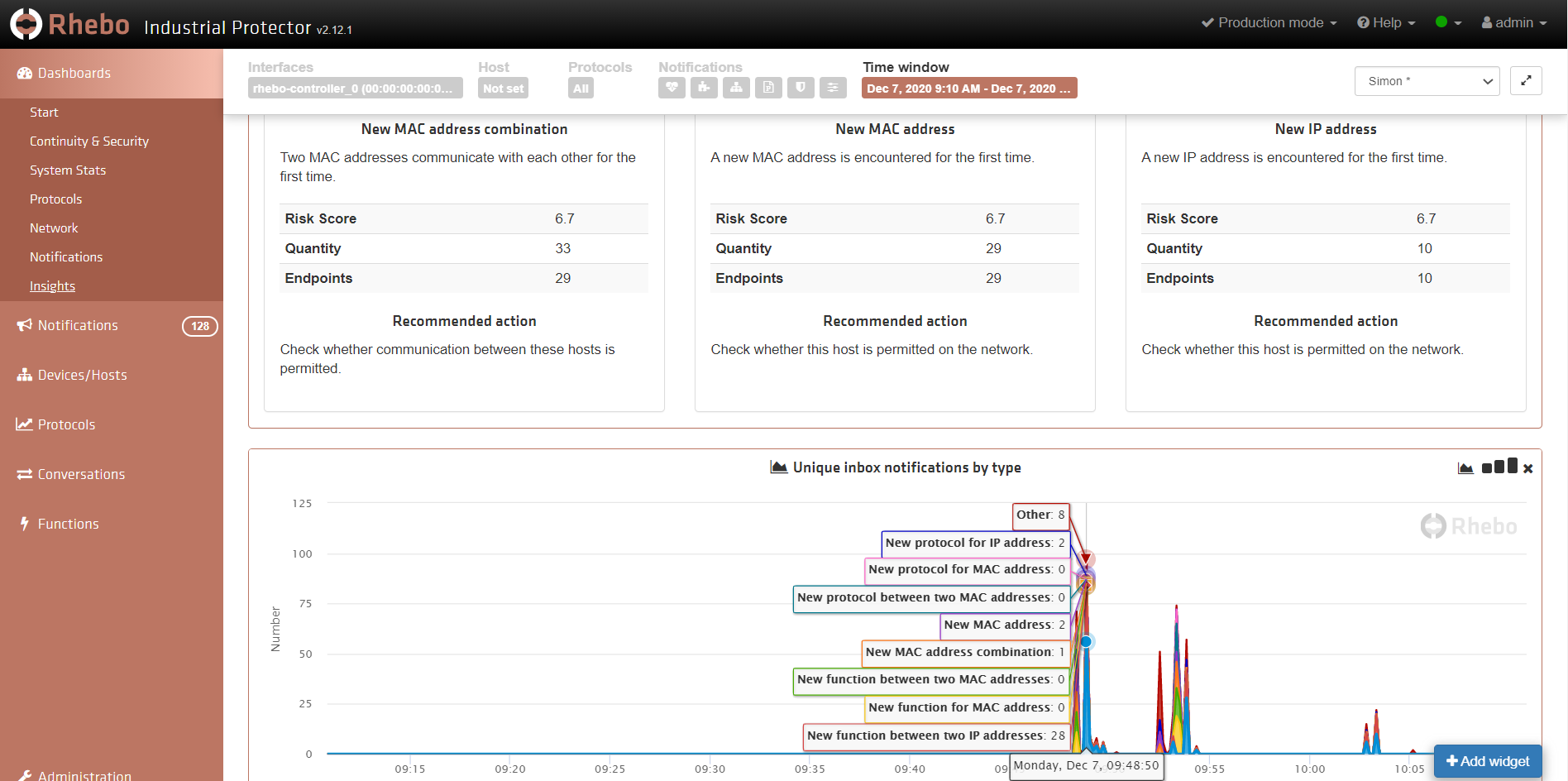
Whereas, NOC/SOC Analysts are more likely to be interested in security information:
How to monitor RIP with PRTG
RIP is also equipped with a REST based API that enables many of the health and performance metrics to be shared with external system, including PRTG. We’ve created a set of Python Script Advanced Sensors to monitor some basic functionality. They are available on our Gitlab page and more information is available on our Sensor Hub (just search for Rhebo). Feel free to use these examples to build your own custom Sensors, using the API documentation available from Rhebo.
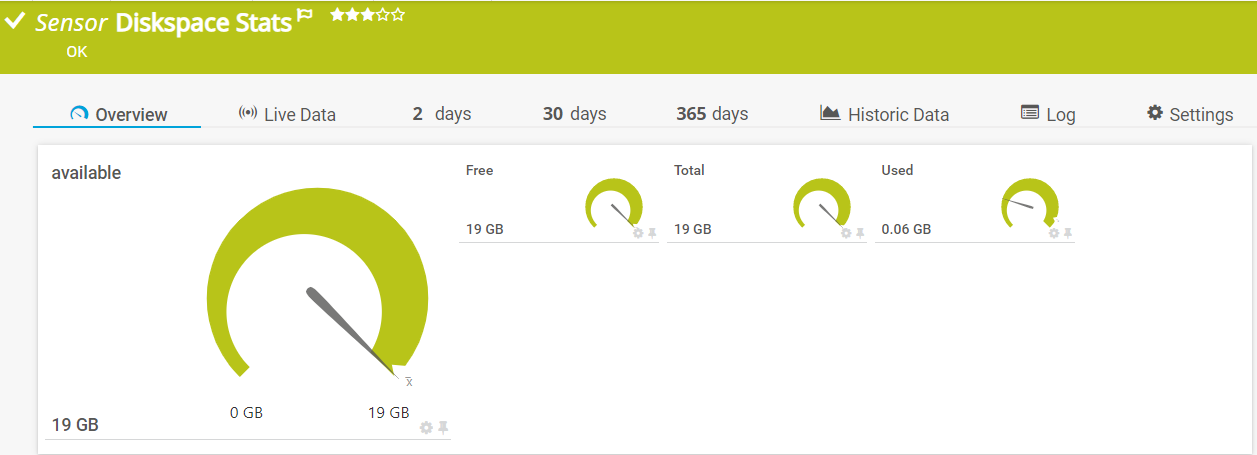
The sample sensors return information about disk usage on the RIP Controller:
Which traffic capture features are enabled:
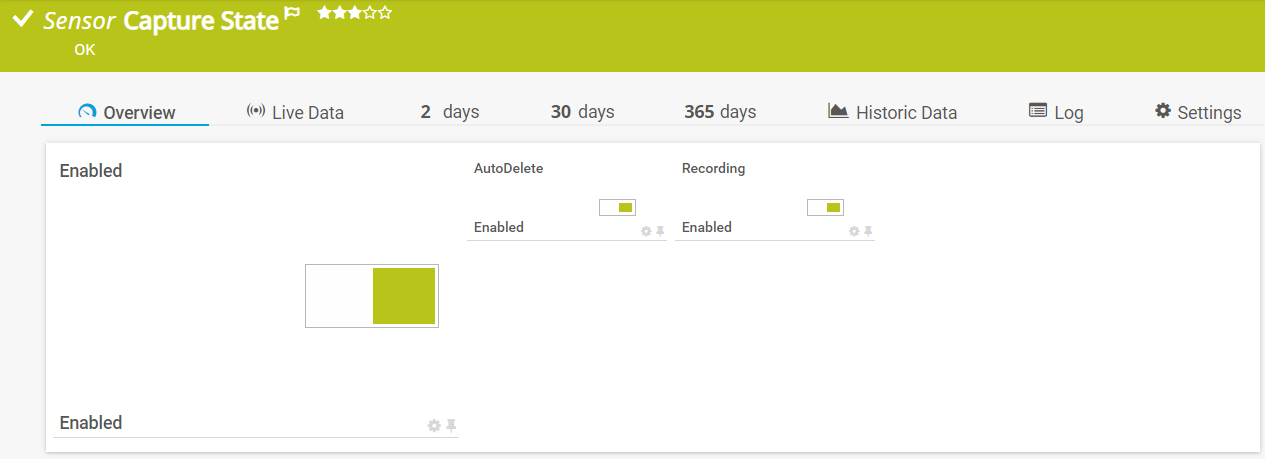
And, of course, the Network Quality Score:
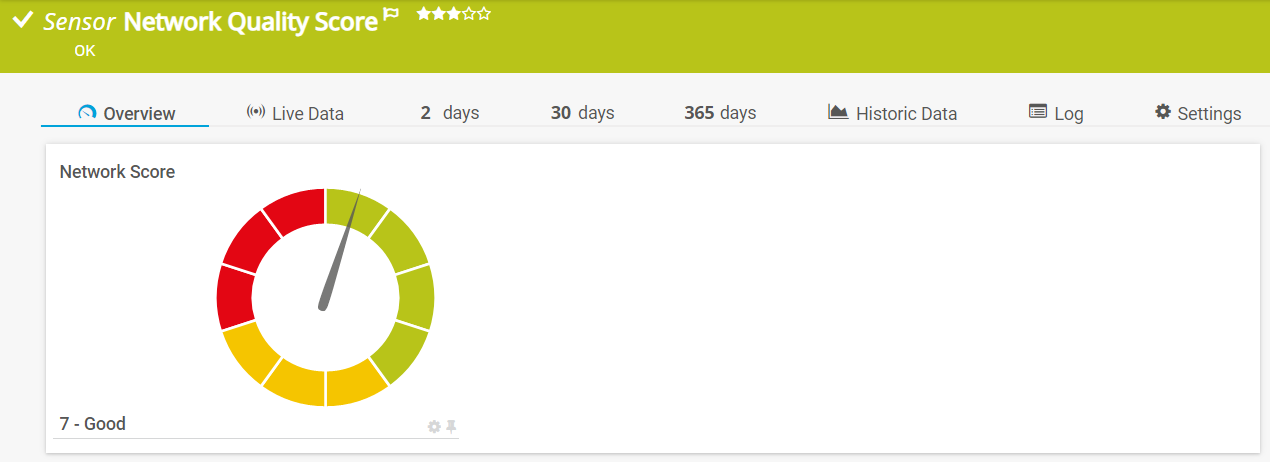
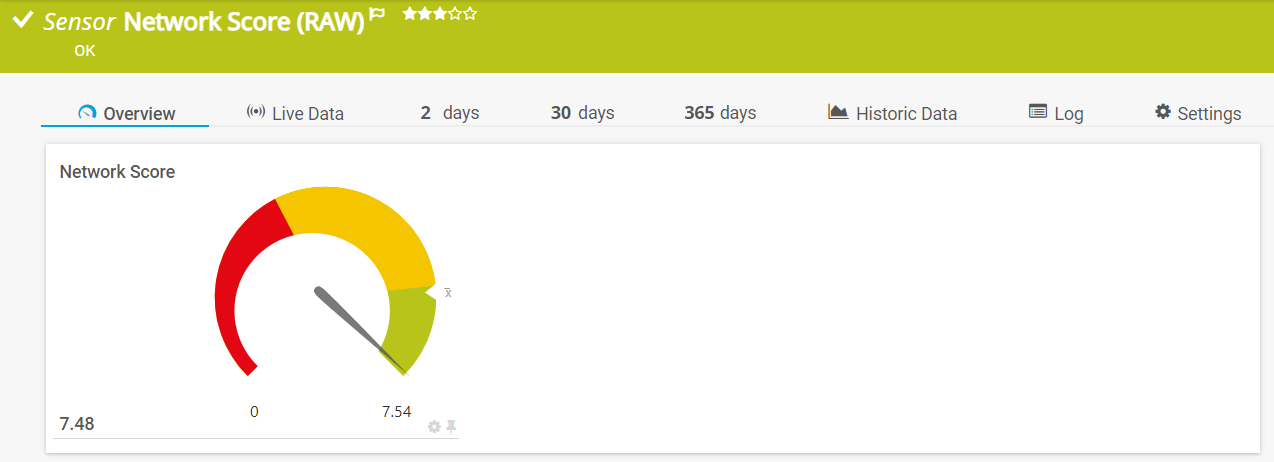
In fact, there are two sensors for network quality: One, shown above, uses a PRTG Lookup to evaluate the Network Score as “Good”, “Medium” and “Bad” according to the calculated value. The second sensor shows the “raw” score, without lookup, which can be used to track the value over time:
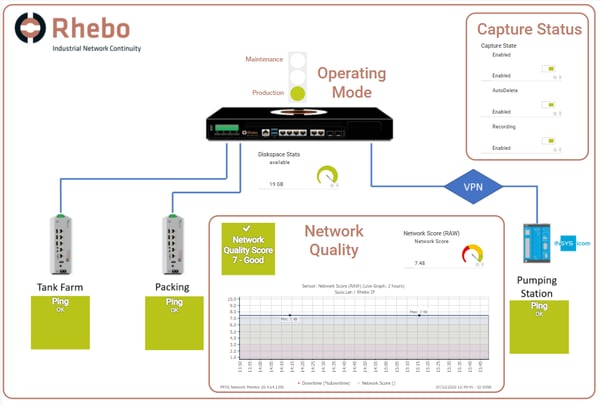
Of course, once you have sensors assigned to your Rhebo Controller, you can then create a map to display the collected data:
As evidenced by the high-profile incidents mentioned in the introduction, OT networks are becoming increasingly popular targets for cyberattack. While the attack methods are often similar to those used to compromise IT systems, the specialized nature of industrial control networks means that IT focused security tools are of little help.
Rhebo Industrial Protector is designed to protect ICS environments and alert OT and NOC / SOC Engineers to any anomalous activity that risks compromising their network. We’ve already looked at several ways in which the worlds of IT and OT differ. But perhaps the biggest is that successfully compromising an IT network is unlikely, in most cases, to lead to physical damage or even loss of life.
 Published by
Published by 




.jpg)