Legacy and modestly-priced network switches may not support flow protocols such as IPFIX, NetFlow (from Cisco, with many versions), jFlow, and sFlow. Still, administrators of older networks and those on a budget must monitor network traffic despite these limitations.
iSNMP stands for Simple Network Monitoring Protocol. Its usefulness in network administration comes from the fact that it allows information to be collected about network-connected devices in a standardized way across a large variety of hardware and software types. SNMP is a protocol for management information transfer in networks, for use in LANs especially, depending on the chosen version. Read more ...
When you’re using switches with no flows, you can still do fine-grained network traffic monitoring using SNMP, port mirroring, and packet sniffing. SNMP is widely supported, and you can augment and tune it using any of several PRTG SNMP sensors. When you reach the limits of SNMP, you can still take advantage of packet sniffing with all its benefits, even in the absence of native network flow support. Here’s how you can get started with SNMP and packet sniffing.
Using SNMP in The Absence of Flow Protocols
Using SNMP Traffic Sensors, you can get metrics for inbound/outbound traffic including those indicating the presence of unknown protocols, which can be indicative of a cyberattack. You can add additional sensors for bandwidth, memory, disks, and files, including threshold triggers, enabling you to gauge the impact of changing metrics on network and PC performance. If your switches support traps, you can also use SNMP Traps.
iBandwidth is measured as the amount of data that can be transferred from one point to another within a network in a specific amount of time. Typically, bandwidth is expressed as a bitrate and measured in bits per second (bps). It refers to the transmission capacity of a connection and is an important factor when determining the quality and speed of a network. Read more ...
When gauging bandwidth, consider using SNMP ifInOctets, ifOutOctets, and if Speed calculations. You can also use PRTG Network Monitor to calculate the bandwidth usage for you. SNMP can alert you to critical loads using the SNMP CPU Load sensor, and it can report on the state of hardware and its operation using the SNMP Hardware Status sensor.
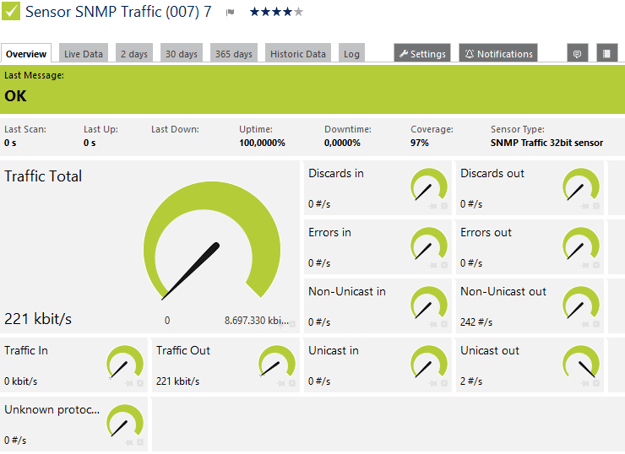

You can use state, speed, volume, and change triggers as well as trigger inheritance to build a system of alerts. Different combinations of alerts appearing together will pinpoint specific events. You could, for example, aid IT security by using a combination of triggers to alert you to symptoms of ransomware, such as the very high volume of extremely rapid file changes that occur when these attacks quickly encrypt mass numbers of files.
Using Port Mirroring, Probes, and Packet Sniffers
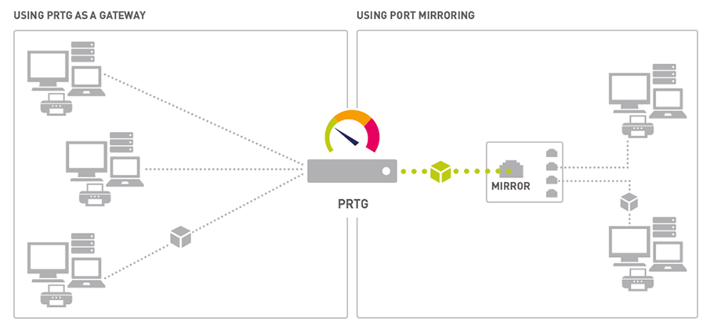
By linking a mirrored switch port to a Windows-based PC running a PRTG Remote Probe, you can add a PRTG Packet Sniffer sensor to achieve detailed traffic monitoring similar to that from network flows. The configuration for this setup is mirror port > standard port on a PC using 2 NIC cards. This configuration is necessary because mirrored ports will often only copy traffic; the probe PC will need a regular switch port to route traffic back to the PRTG Core Server.
This kind of port mirroring and traffic sniffing enables you to monitor a variety of traffic and protocols. These protocols include IRC/Chat, Citrix, FTP or P2P file transfers, network services (DHCP, DNS, ICMP), email, NetBIOS, Remote Control (SSH, RDP, VNC), HTTP(S), UDP, and TCP just as you would with network flows. If you add a tcpdump, you can also track BitTorrent (and related bandwidth abuses), ARP, SIP, and RTP traffic.
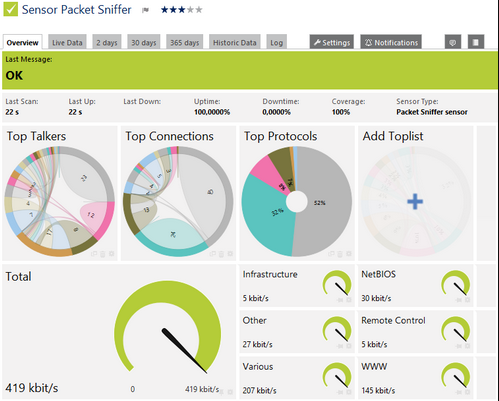

You can use this packet sniffing configuration to isolate network bandwidth bottlenecks and bandwidth hogs. In addition, by correlating bandwidth with other anomalies you can detect potentially illegal traffic related to media rights violations, attack traffic, or botnet C&C servers that use IRC, which are used for DDoS attacks.
 Published by
Published by 











