Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say.
(Edward Snowden)
Our ideas of privacy and freedom have changed with the Internet. In earlier times, thoughts of freedom were enshrined in constitutions to protect us against tyrants and menaces. In our digital lives, there are complex threats and the laws that have been written to protect us belong to times no longer linked to our realities. The protection of your digital rights is an individual, personal undertaking. This is part 2/2. Find part 1 here, which covers achieving 30% and 60% anonymity.
3 remarks on this article:
- I will provide step-by-step instructions for different audiences. Some people only want to protect their most sensitive data, while others want to move around the Internet completely anonymously. I'll show you in ascending order and with simple steps, what needs to be considered.
- Anonymity and overall security go hand in hand. If you neglect the security of your devices, it directly affects the integrity of your personal information.
- This article does not advocate not disclosing any data about yourself on the Internet. It is about being able to decide freely and independently which data is disclosed.
Let's continue the journey.

Become 90% anonymous
Now things are getting a lot more serious.
📥 PGP
PGP stands for Pretty Good Privacy, is used for the encryption of email communication and ensures the integrity of emails with signatures. If you use ProtonMail (see part 1/2), you automatically communicate PGP-encrypted to another ProtonMail address, and you can view your PGP keys in the settings. Of course, it is also easily possible to encrypt messages from other email providers with PGP. There are several freeware options available for Windows, macOS, Linux, and Android.
A few notes for PGP beginners:
- Your recipient's public key is required to encrypt your email. Public keys are therefore not secret. They can often be found on key servers, or you simply ask your recipient. You can also attach your public key to outgoing emails.
- Your private key is called private because it is for your eyes only. It's used to decrypt an email, which was encrypted using your public key.
- A public key fingerprint simplifies the whole public key thing; it's a short sequence of bytes used to identify a longer public key.
- Once set up, sending and receiving PGP encrypted messages is effortless.
Here's an appealing YouTube video to illustrate the basics of PGP once again.
To use PGP you need software based on OpenPGP or GnuPG.
iWait... What? 😵
"PGP", "OpenPGP" and "GnuPG" (often simply called "GPG") sound similar and are often used interchangeably, even if this is wrong. PGP is probably the most commonly used term. From this software, the open standard OpenPGP for the confidential and integrity-secured transmission of data was derived. An important, well-known implementation is the open source project GnuPG (Gnu Privacy Guard). GnuPG also supports the use of smart cards and OpenPGP keys for SSH. All this goes back to the early developments by Phil Zimmermann in 1991. His very first version of PGP included an encryption algorithm called BassOmatic.
It makes sense to accept standard software suggestions when generating keys, so that problems when sending encrypted e-mails are avoided as far as possible.
- Outlook can at least be taught rudimentary PGP. GnuPG must be pre-installed, for example with GPG4win. The free Outlook Privacy Plugin tool then integrates GnuPG into Outlook.
- Apple only supports the S/MIME standard in its mobile operating system iOS for end-to-end encryption. PGP does not work natively on iPhones and iPads. GPG Mail, as part of the GPG Suite, integrates the full power of GPG seamlessly into macOS Mail.
- There are several usable and secure PGP implementations on an open source basis for Android that you can use in conjunction with mail apps (via the OpenPGP API). The most common are Android Privacy Guard and OpenKeychain. By far the most widely used PGP-secured emailing app for Android is K9-Mail.
i⚡☠️ Efail: Why encrypted emails are at risk Unfortunately, in connection with the security gaps in encrypted emails named Efail, a lot of misleading information can be found. The bad news: This is not only a problem in email clients, but rather a systematic problem. It has now become clear that GnuPG is much more affected than OpenPGP, because the latter provides various ways to avoid attacks. The good news: unlike S/MIME, the OpenPGP standard includes procedures to prevent message manipulation - the so-called Modification Detection Code (MDC). This method is rather unusual from a cryptographic point of view, but at least so far there are not any known security gaps in MDC itself.
📂 File Sharing
Cloud storage services like Dropbox, which are designed to let you share files with others very conveniently, are "very hostile to privacy". Fortunately, there are workarounds.
OnionShare is a comparably easy-to-use but very secure alternative. With OnionShare you can anonymously share files of any size; it's available for MacOS, Windows, Ubuntu and Fedora.
For the use of the software, the application starts a server with an onion service and associated address on the user's computer. Third parties can then access this address via the Tor browser and upload or download files.
The random long address generated by OnionShare uses version 3 of the Onion addresses. One option also allows the older, shorter v2 addresses to be used. Firewalls and NAT do not play a role in this case because the service connects to the Tor network. That the onion addresses use HTTP is also acceptable, since Tor services are end-to-end encrypted anyway. Since the local computer hosts the files, the upload and download speed depends on the local network. If the local laptop is closed or sharing is aborted, the file exchange is also stopped directly. However, this also happens automatically as soon as someone has downloaded the file. If you want to share it with a group, you have to select this explicitly.
If for some reason you don't like OnionShare, there are alternatives.
- Using WebRTC, FilePizza eliminates the initial upload step required by other web-based file sharing services. Because data is never stored in any intermediary server, the file transfer is fast, private, and secure.
- RetroShare is an open source cross-platform, private and secure decentralized communication system. It lets you to securely share different files.
🕵️♂️ a new digital identity
Let's get to a part that is really fun: the creation of a new digital identity. Above 90% anonymity you are beyond using your real name. And if you don't want to do without various platforms that require registration with a name, you can't get to this level. Either you get creative yourself or you use a tool like the Fake Name Generator.
First you create an email address for your new identity (and take a provider from the list in part 1/2). Then use your new identity always with exactly the same accompanying data, such as birthday details.
Some platforms don't like it if you register with a fake name and may even block you. So don't be offended if Mark won't let you join his club; it's for your own good.
You also might want to use your new identity consistently. The more often you log in somewhere with your invented data, the stronger and more believable this identity will become. Don't break character and die with the lie.

The last 10%
The last 10% is hard to achieve. If you push this whole "being a ghost" thing so far, you probably have a reason for it. And that doesn't have to involve something illegal - in our understanding of the word. If I were a whistleblower or a political dissident, this is the way I would do it.
🔳 Tails AND QUBES OS
Edward Snowden and Glenn Greenwald have given Tails a relative prominence.
- Tails is a live operating system designed to maximize your anonymity. It helps you to use the Internet almost everywhere and anonymously from any computer.
- It is a complete operating system that is booted directly from a USB stick or DVD, regardless of the operating system installed on the computer. It is freeware, based on Debian GNU/Linux.
- Tails includes various programs that have been pre-configured with security in mind: a web browser, an instant messaging client, an email program, an office package, etc.
- In part 1/2 I mentioned the problem that when using Tor it can never be excluded that background programs communicate with the Internet unencrypted. This problem is almost completely eliminated with Tails as it only allows connections via Tor; all other attempts are strictly blocked.
- A big disadvantage: Tails is no fun to use. It is cumbersome, slow, and offers only the absolute basic functions to communicate anonymously and exchange certain documents. Truth be told: Tails isn't a nice thing to look at.
Additionally, here's a great YouTube tutorial for installing tails (on a USB stick).
If you are enthusiastic about the anonymity of Tails, but don't want to miss the relative comfort of a "normal" OS, I can strongly recommend Qubes OS. It takes an approach called "security by compartmentalization", which allows you to compartmentalize the parts of your digital life into isolated elements called "qubes".
- This approach is also "security by isolation". The assumption is that there can be no completely bug-free, perfect desktop environment. One critical bug in one interaction may be enough for malicious software to take control.
- In Qubes, the isolation is provided in two dimensions: hardware controllers can be isolated into functional domains, whereas the user's digital life is divided into domains with different levels of trust. Each of those domains is run in a separate virtual machine.
- Qubes is not a multi-user system.
- Qubes has a somewhat nerdy, pleasing UI. Compared to Tails, it's even a real beauty.
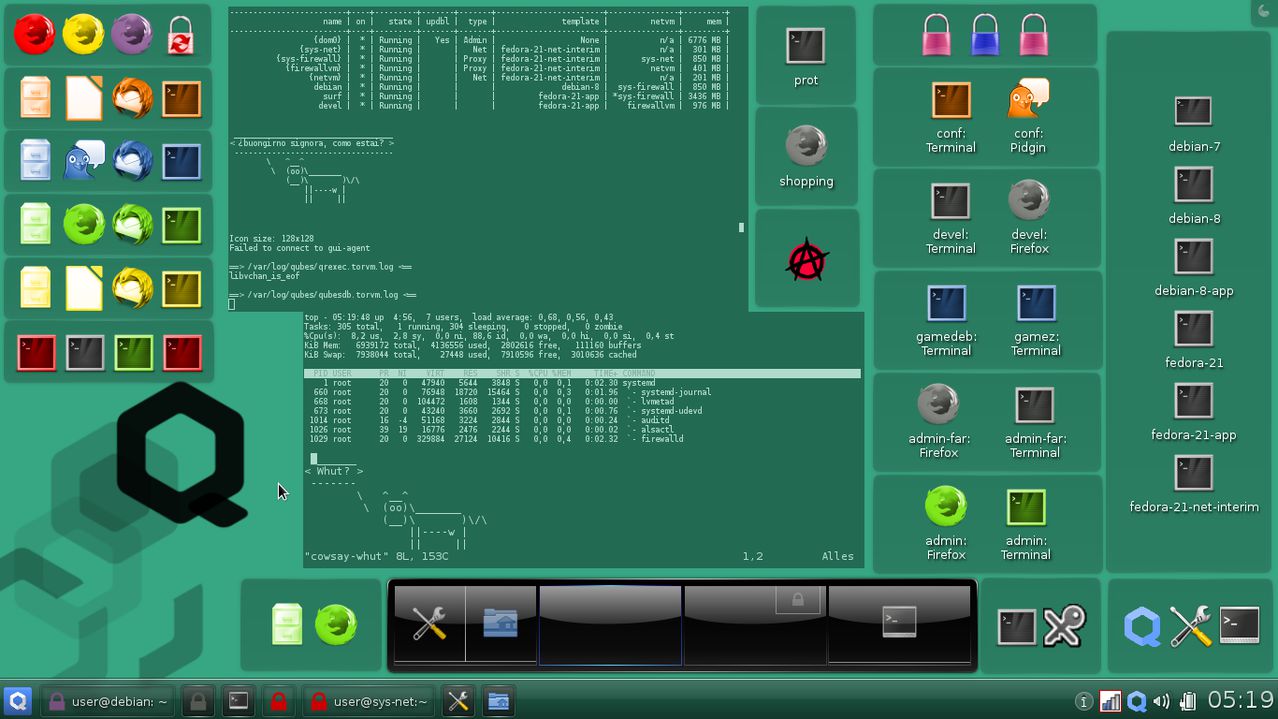
If you're serious about security, @QubesOS is the best OS available today. It's what I use, and free. Nobody does VM isolation better. https://t.co/FyX5NX47cS
— Edward Snowden (@Snowden) 29. September 2016
💻 Your Hardware
Your hardware can be traced back to you. If you bought it online and/or with your credit card, you could theoretically integrate as many security mechanisms into your digital life as you like: the clear reference to your actual identity is always immanent. The only way out would be to purchase all technical devices that communicate over the Internet in cash or using a cryptocurrency. These are rather high-level considerations; nevertheless, it's doable.
😈 The Devil Lies in the Detail
Ultimately, you need to perform the steps mentioned above without any exceptions.
- You must never communicate with your friends or family again using any device that reveals your true identity.
- You must never again use a platform with which you are registered under your real name. This includes all platforms that request your mobile phone number.
- If you wish to use a platform or online service that requires a real ID for authentication when you register, you are screwed. You would have to think about ways of transforming your fictional identity into a real one. This is far from impossible, but might involve steps that fall under criminal law in your country. Within the framework of an artistic project, one guy (using a purely fictional identity) pushed the whole thing pretty far - while documenting it.
🥳🎉🎊 That's about it. No matter if you aim for 30% or 90% anonymity: I checked the math and both are more than 0%.
In the end, a hopefully indisputable remark: companies and organizations of all sizes should have an equally strong interest in protecting the privacy of their (potential) customers. This concerns the active collection of information and the management of data entrusted to the enterprise in question. Gartner writes about Digital Ethics and Privacy (as one of the Top 10 Strategic Technology Trends for 2019):
Privacy risks matter to businesses because the individuals whose privacy they guard are their employees, customers, patients, consumers (...). If individuals discover that an organization has violated their personal privacy, it will affect how they view and relate to that organization. For example, individuals may become less loyal to their employer (...) or less likely to trust their healthcare provider or government.
Any thoughts, wishes or suggestions? Feel free to use particularly extravagant fake names for commenting!
 Published by
Published by