Hello fellow sysadmins! Let's dive into the wonderful (and occasionally hair-raising) world of SNMP polling. If you've been in the field for a few years, you've probably wrestled with SNMP at some point. Whether it was configuring a Cisco router or troubleshooting a community string mismatch, SNMP can be both a lifesaver and a headache. But love it or hate it, it's essential to keeping our networks up and running. So let's break it down in a way that speaks to you as someone who's been in the trenches.
What is SNMP polling anyway?
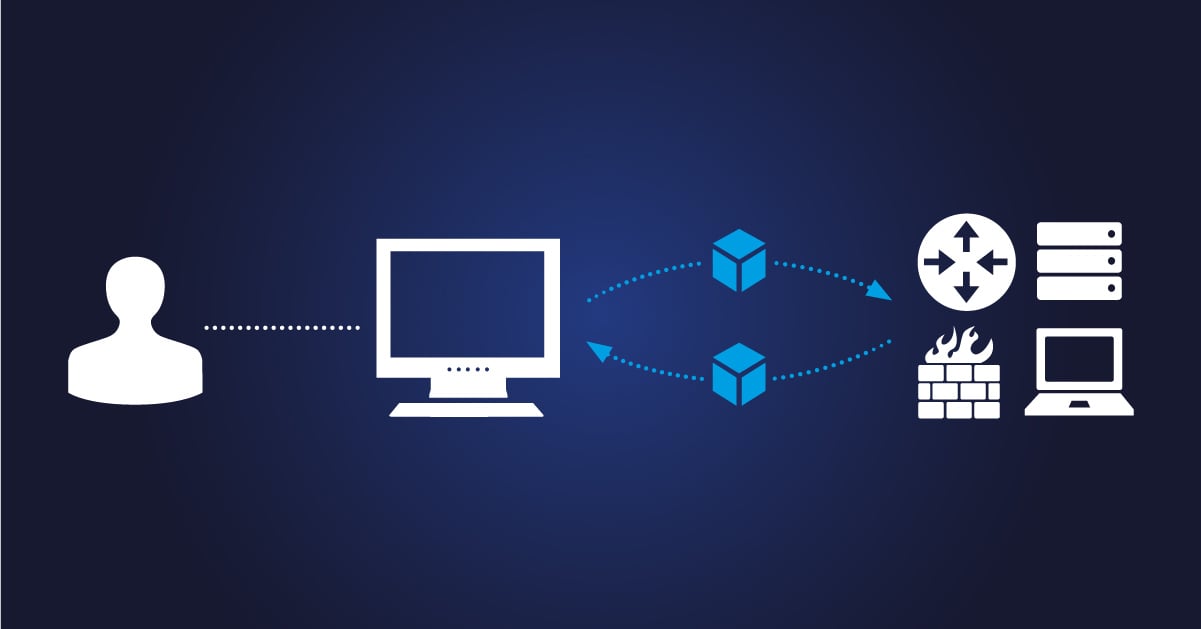
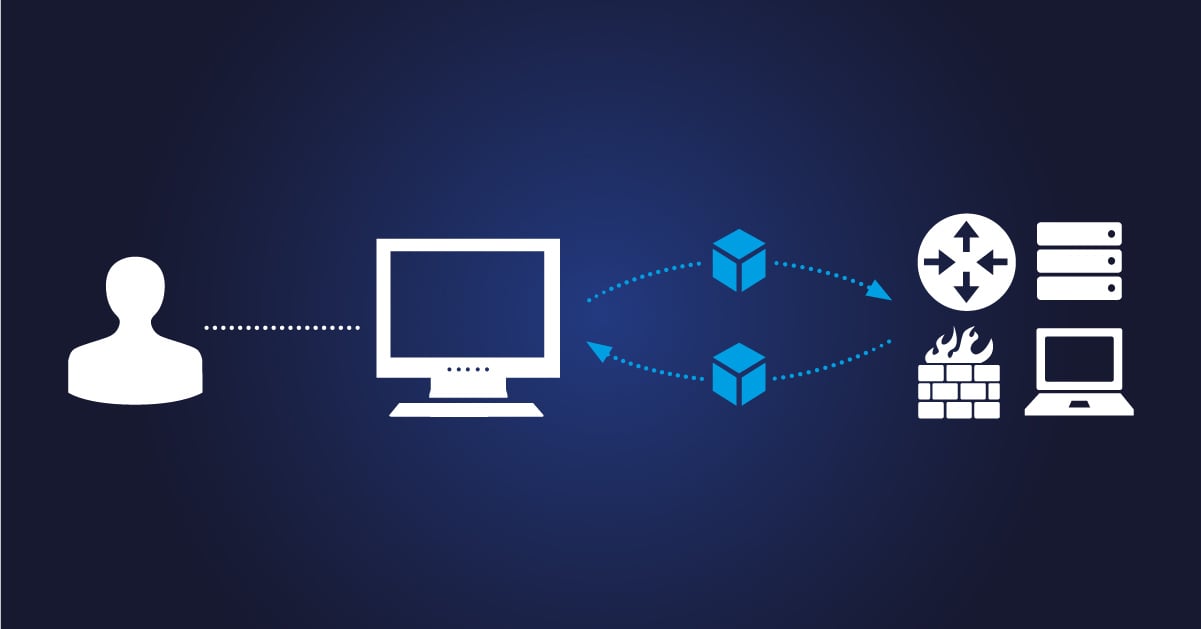
SNMP, or Simple Network Management Protocol, is the language that lets your network devices (like routers, switches, and firewalls) talk to your network monitoring systems (NMS). Polling is the process where your SNMP manager (or management station) asks the devices, "Hey, how are you doing?" and the devices respond with their metrics.
Think of SNMP polling as your regular health check. The SNMP manager sends out a request (usually a get-next), and the device responds with data, from its Management Information Base (MIB)—basically a database of all the stuff the device can report. Each piece of data has an Object Identifier (OID), which is a unique address in the device’s data universe.
SNMP polling vs SNMP traps: What’s the difference?
If SNMP polling is you actively checking in, SNMP traps are the devices screaming, "Help! Something’s wrong!" without being asked. Both are useful, but polling gives you more control—you decide when and what to ask for. With traps, you’re relying on the device to raise the flag. Spoiler: not all devices are good at it.
How SNMP polling works: the nuts and bolts
- SNMP Agent: Installed on the device (e.g., a Cisco router), it’s responsible for responding to requests.
- SNMP Manager: The boss—it sends SNMP requests and collects the data.
- Transport Protocol: SNMP mostly uses UDP (because who needs reliable delivery, right?).
- Authentication: Depending on your setup, you’ll use a community string (for SNMPv1 and SNMPv2c) or something more robust like SNMPv3 credentials.
Why SNMP polling matters
Here’s why you should care about SNMP polling, even when it makes you want to pull your hair out:
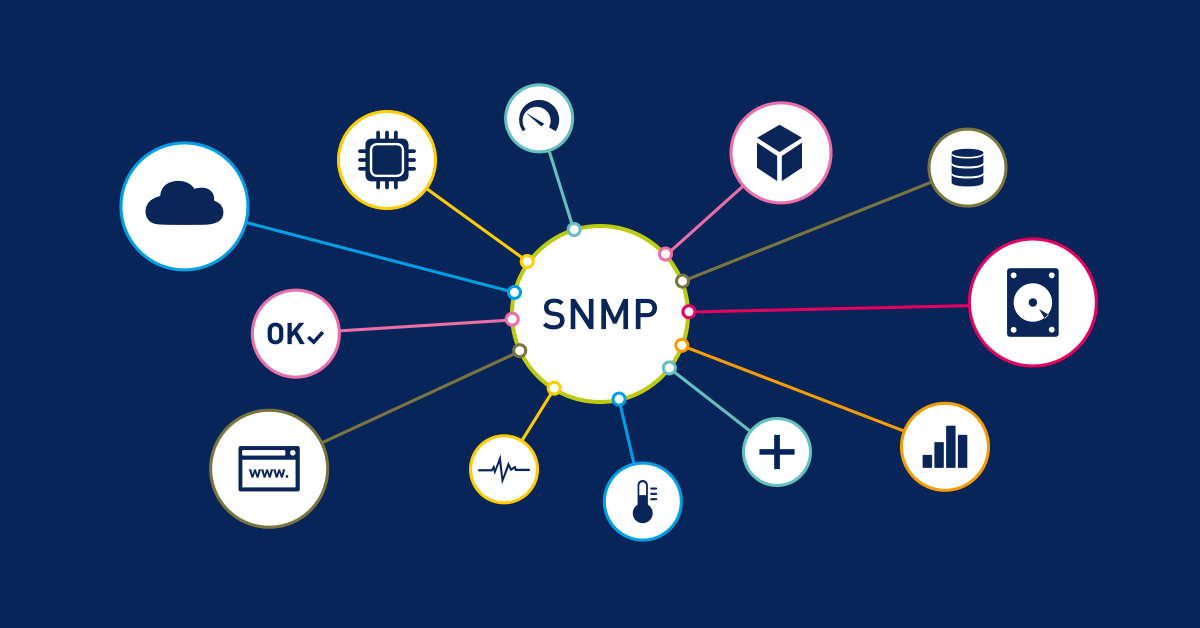
- Real-time monitoring: Polling gives you up-to-date info on your network devices. Whether it’s the CPU usage of a server or the bandwidth on a router, you’re always in the loop.
- Proactive troubleshooting: Spot issues like high CPU usage or near-capacity bandwidth before they cause outages.
- Customization: You can decide which metrics to monitor based on your needs. Want to check the firewall's open connections? Grab the right OID from the MIB and you’re golden.
SNMP polling: the versions (it’s complicated)
SNMP has more versions than some operating systems. Here’s the rundown:
- SNMPv1: The OG. Simple, but about as secure as leaving your router’s default password unchanged.
- SNMPv2c: Adds bulk requests for efficiency but still relies on the trusty community string for security.
- SNMPv3: The superhero of the SNMP world with access control and proper authentication. (Use this if you like sleeping at night.)
Best practices for SNMP polling
- Choose the right version: Use SNMPv3 whenever possible. It’s secure and supports encrypted communication.
- Optimize polling intervals: Polling every second might sound cool, but it’ll wreck your bandwidth and overwhelm your monitoring systems. Start with 5-10 minutes and adjust as needed.
- Configure SNMP correctly: Whether it’s on a Cisco device or a third-party appliance, make sure your SNMP settings align with your network’s security policies.
- Use templates: Many monitoring software solutions offer SNMP templates for common devices. Save yourself the hassle of manually configuring every OID.
Common pitfalls and how to avoid them
- Community string missteps: Treat your community string like a password—use something strong and unique. "public" is a big no-no.
- Firewall blocks: Ensure your firewall rules allow SNMP traffic. (Ports 161 and 162, for the curious.)
- Outdated MIBs: Devices update their MIBs; your NMS should too. Using old MIBs is like trying to read a map from the ‘90s.
SNMP walk: your debugging lifesaver
When you’re troubleshooting SNMP, the snmpwalk command is your best friend. It walks through the MIB, fetching all available OIDs. It’s like opening the fridge to see what’s inside instead of guessing.
Paessler PRTG: simplifying SNMP polling
If SNMP polling feels like a chore, Paessler PRTG has your back. With built-in SNMP sensors, customizable dashboards, and support for all versions of SNMP, it takes the guesswork out of network monitoring systems. Plus, its ability to integrate with API and handle data from syslog makes it a one-stop shop for your monitoring needs.
Final thoughts
SNMP polling isn’t glamorous, but it’s the backbone of effective network monitoring. With the right tools, a little patience, and the occasional snmpwalk, you can turn it from a chore into an indispensable part of your toolkit. And hey, if you’re still struggling, remember: every sysadmin has cursed at a community string at least once. You’re in good company.
Ready to level up your SNMP game? Try PRTG Network Monitor free for 30 days and experience hassle-free SNMP monitoring.
 Published by
Published by