Every inbound DDoS is also one of more outbound DDoSes. Outbound DDoS may not fill up the pipes or take critical services offline but if we are to stop cyber criminals, we have to work together and the time is now to be that friendly network neighbor.
Everyone under attack wishes that the source of the outbound DDoS would do something about it. Attackers are working together, so should we but unfortunately we don’t design and maintain networks together. It’s high time to go above and beyond the call of duty.
Outbound DDoS arise from malware on the network. As a measure of urgency, operators should be empowered with better viewpoints to detect malware and troubleshoot the elaborate world of cyber criminality efficiently. It’s hard to see the forest when you are standing in the middle of it staring at a tree.
As a result, we must aid them with appropriate tools such as Scrutinizer to combat the rising level of outbound DDoS activity resulting from malware and compromised hosts. DDoS comes and goes but the key is not to get tricked due to lack of good visibility tools.
Moving Away From Inbound DDoS
Every type of network gets hit by DDoS, from small business to large enterprises. For example, universities are packed with students coming and going with multiple device types, a variety of traffic flows and types exists on their networks. As a matter of policy, many universities have an open security standard. They see this as part of their mission for students to have unfiltered Internet access.
As a result, many student devices get enlisted into an outbound DDoS without ever knowing. Outbound DDoS is a matter of grave concern. Therefore, it’s time to stop fiddling while Rome burns. With limited visibility tools, the compromised end hosts have no idea they are controlled and part of a Botnet swarm.
In the early days of the Internet, it was common for a university to be given a full /16. As a result, the internal Dynamic Host Configuration Protocol (DHCP) ranges consist of unfiltered routable address. The reachability of the systems within the university space is high making them the prime targets for both inbound DDoS and the malware responsible for outbound DDoS.
Millions of routable addresses is not that much to scan. It's not difficult to find vulnerabilities in a /16 or even a /8 for that matter. If the move to IPv6 was made without a hitch, there may not be too much of a problem as it’s much harder to find vulnerabilities with billions of IPv6 address. However, the move to IPv6 is not the case for many organizations creating a bubble for outbound DDoS.
Only As Strong As Your Weakest Link
Staff come and go in all organizations. Some enlist in short-term employment and inherit workstations from previous employees that are not properly sanitized. There is churn at any organization. Even more the case at universities. As a result, security problems are compounded from one year to the next.
Have you ever heard of the machine that's online for 20 years? No one knows where it is but it can be pinged. A 20-year-old computer might not have enough juice for a heavy hitting DDoS attack but it can be used as an entry point for a bad actor becomes as comfortable as an old shoe for the attackers to stamp their feet and launch an outbound DDoS attack.
With security, you are only ever as strong as your weakest link. Front-end web service may be hard tuned but an old unpatched server on the same segment leaves the window open for compromise.
Many tiered application designs don't have appropriate firewalling between segments. Databases and front end application servers could be sharing the same Layer 2 or Layer 3 segment with no security between tiers. The bad actor finds ways to laterally move throughout the network, known as beach heading. This enables an adversary to reach and compromise hosts that are not otherwise exposed to attack and so may not be as hardened against attack, and in turn gives bad actors additional resources to perform actions including stage attacks against others outside the network.
Once an adversary has hold of your infrastructure it's easy for them to launch an outbound DDoS. Getting in is the hard part but readily available tools make outbound DDoS a simple task.
Outbound DDoS
One way to find out if you are having an outbound DDoS is to determine if there are lots of IP’s on the network that you should not be routing. Outbound DDoS use false source IP address hiding the identity of the sender. This is simple to address, but many network operators don’t think to. Is egress filtering configured to drop spoofed addresses? Doing so would stop these attacks in their tracks.
iAn IP address (internet protocol address) is a numerical representation that uniquely identifies a specific interface on the network. IP addresses are binary numbers but are typically expressed in decimal form (IPv4) or hexadecimal form (IPv6) to make reading and using them easier for humans. Read more ...
There are generally-accepted practices for some aspects of designing and maintaining networks, but they don't cover everything. Vendors just supply products for smart engineers to design a network. It's up to the individual preference of the designer as to how he or she creates the architecture. As a result, we are left with billions of unique networks that are unique snowflakes. This is not anyone's fault. Every network has its own issues and problems to work around, and there’s no one right answer to those problems, so everyone solves differently.
The Art Of Troubleshooting
Billions of unique snowflakes lead to a wide variety of security vulnerabilities which at some point require troubleshooting. Further, the challenge is compounded by the fact that troubleshooting lacks a science which is based on the logic that prevention is better than cure. Both network design and troubleshooting is an act of art controlled by individual preference.
There is too much variation and much is left to the hands of the gods especially when traditional visibility tools are employed. Visibility is necessary for troubleshooting, and the visibility tool needs to be flexible to handle a variety of environments.
If the operators are not imparted with the appropriate visibility tools from the start, it's a losing game.
Stone Age Methods To Outbound DDoS
An outbound DDoS exhibits a lot of bandwidth coming from a compromised or impossible source and with the right toolset the anomalous behaviour is easily spotted and tracked. The stone-age practice would involve checking interface activity with Simple Network Management Protocol (SNMP) and then carry out an intrusive full packet capture to determine which source is generating that traffic.
iSNMP stands for Simple Network Monitoring Protocol. Its usefulness in network administration comes from the fact that it allows information to be collected about network-connected devices in a standardized way across a large variety of hardware and software types. SNMP is a protocol for management information transfer in networks, for use in LANs especially, depending on the chosen version. Read more ...
Analyzing SNMP state can help to some extent but it's not the cutting-edge way to deal with DDoS. Without the insights from flow technologies, it's going to be hard to pinpoint accurately.
SNMP informs of an attack but won't tell you precisely who is getting attacked, or who by. NetFlow, on the other hand, holds the sweet spot zone between SNMP and low level monitoring of full packet captures. It sharpens the operator’s focus upon an outbound DDoS.
To successfully stop outbound DDoS, operators must be armed with the correct visibility solution. NetFlow puts operators in the strongest position upon a DDoS event.
NetFlow Tackling Outbound DDoS
NetFlow and other telemetry sources play a big role in cybersecurity. Knowing is good but knowing everything is even better. NetFlow provides comprehensive visibility into all network traffic that traverses a supported device that support NetFlow technology such as routers, switches and other infrastructure devices.
For outbound DDoS troubleshooting, NetFlow offers administrators a granular kit with the ability to identify with a fair amount of precision what is being attacked and furnishes detailed properties about that attack.
The combination of protocol information means you can identify a wide variety of vectors. For example, DDoS null attacks have no port state attempting to circumvent common firewall filtering. Other examples may include packets that have no protocol set.
The RST flood attempts to reset existing connections which are more of a nuisance than a heavy pipe filling event. All these types of attacks stick out like a sore thumb in NetFlow as their TCP flag patterns are very distinctive when compared to legitimate traffic.
Visibility at this level allows the setting of thresholds, enabling early heads up before it rises to the level where it would be visible with an SNMP monitor. This is critical when looking for outbound DDoS, which often is not a large portion of traffic at the source.
NetFlow performs session level annotation of all the flows. Session level annotation makes it simple to monitor what type of traffic on your network should and shouldn't be. Flows are geo-tagged with country code, AS number and other local information making it easier to detect any out-of-place traffic. If both the source address and destination address of a session are not internal, then you know that it’s not valid and can resolve to terminate the spoof right at the gates. This facilitates the administrators to be that friendly network neighbor.
NetFlow detection uses traffic groups, which organize the traffic by logical known space to identify where the flows came from. Even if someone is trying to evade detection by spoofing source IPs, NetFlow alarms by giving details on interfaces the flow traverses. This offers an ideal method to track and identify whether the routing devices internal to the network are performing egress filtering.
Summary
The first step to combat an outbound DDoS is to have the right map of the network. The first requirement is the accuracy of that map. Having poor network visibility is just like walking around in patchy fog. We are going to see a major network fall from a cyber attack in the next 12 months. The global system is interdependent on creaky pieces of legacy systems. The foundations are not about to change and something is going to give way.
NetFlow enables operators to organize the network with a clear picture to shine when abnormal events occur. It helps operators better understand the function of the overall system and heightens security.
Like a frog slowing and boiling in the pot, we need to realize when the waters are getting hotter and it’s time to jump out. NetFlow is the tool that blows the whistle when we are approaching the boiling point and notifies the course of action to dismantle the outbound DDoS attack.
 Published by
Published by 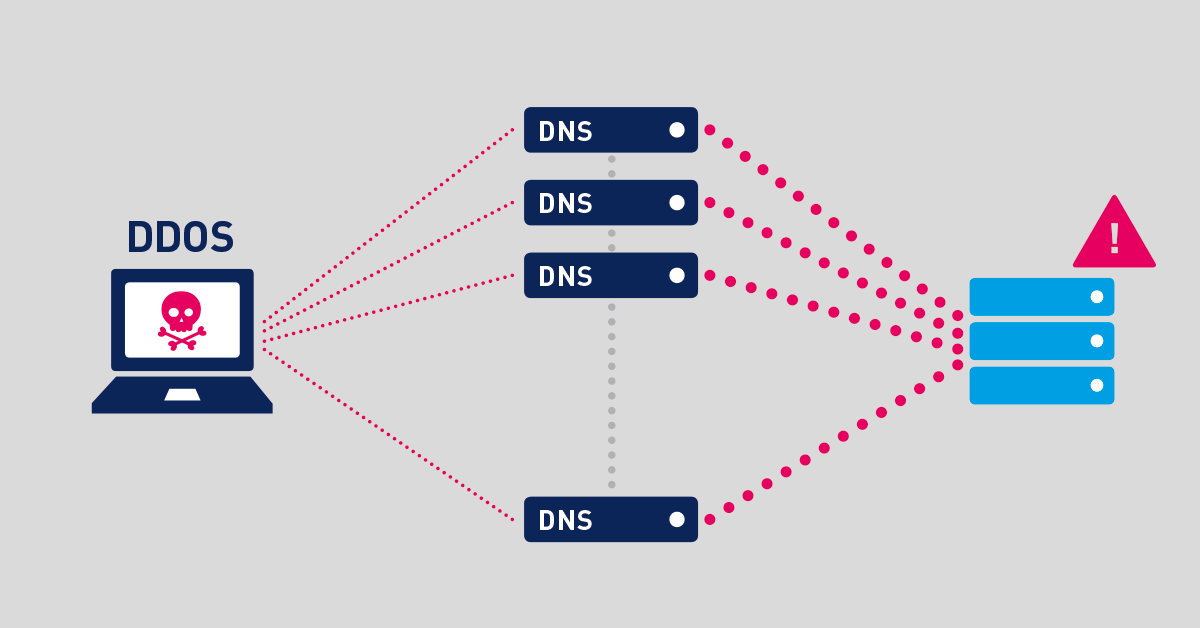




.jpg)