You are probably familiar with Palo Alto Networks based in Santa Clara, California, who provide their 45,000+ customers in over 150 countries a "Next-Generation Security Platform" through their firewalls and security management tools. But did you know that Paessler PRTG can monitor the critical aspects of a Palo Alto device quickly and easily?
Palo Alto Networks firewalls are critical security infrastructure components that require comprehensive monitoring to ensure optimal performance and security posture. With a multi-protocol approach, PRTG can monitor your firewall performance, security events, VPN connections, and traffic patterns from a single dashboard.
It's great to have an industry-leading security appliance in place, but what if the device or network connected to it has an issue? How do you maintain visibility of your Palo Alto devices along with the rest of your network simultaneously? How can you monitor your Palo Alto devices to ensure they are performing adequately and providing the level of protection you expect?
Why Monitor Palo Alto Firewalls?
Effective Palo Alto firewall monitoring helps prevent security breaches, ensures compliance, and maintains network performance. Key benefits include:
- Security threat detection - Monitor failed authentication attempts and policy violations
- Performance optimization - Track CPU usage, memory consumption, and session counts
- Compliance reporting - Generate reports for security audits and regulatory requirements
- VPN tunnel monitoring - Ensure IPsec and SSL VPN connectivity remains stable
- Proactive maintenance - Receive alerts before issues impact network operations
PRTG Palo Alto Monitoring Methods
PRTG offers multiple monitoring approaches for Palo Alto firewalls, each providing different insights into your firewall's operation.
SNMP-Based Palo Alto Firewall Monitoring
iSNMP stands for Simple Network Monitoring Protocol. Its usefulness in network administration comes from the fact that it allows information to be collected about network-connected devices in a standardized way across a large variety of hardware and software types. SNMP is a protocol for management information transfer in networks, for use in LANs especially, depending on the chosen version. Read more ...
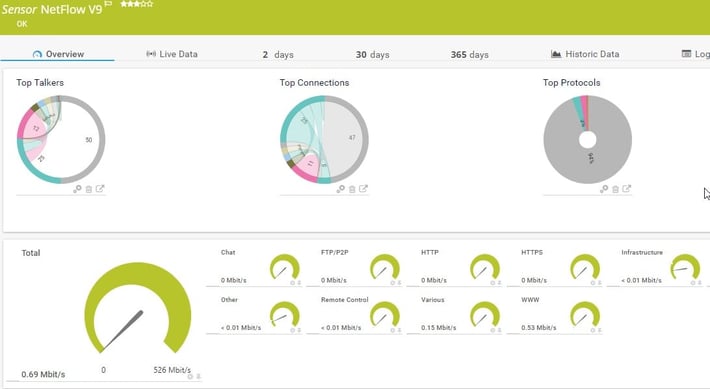
Palo Alto devices are Linux based and support SNMP v2c and v3 (find out more about SNMP monitoring with PRTG here). Palo Alto also supports syslog messages and SNMP trap forwarding to an SNMP management station or syslog receiver. Along with these monitoring components, the ability to capture Netflow V9 packets for an aggregate view of bandwidth consumption by device, connection and protocol is also included.
To configure SNMP monitoring:
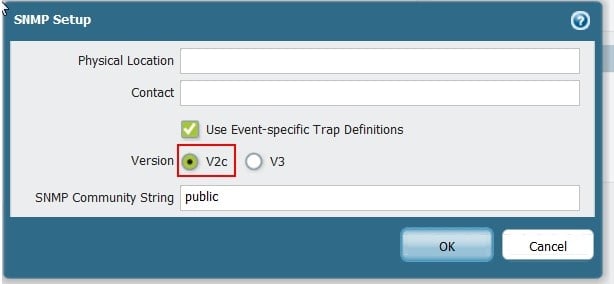
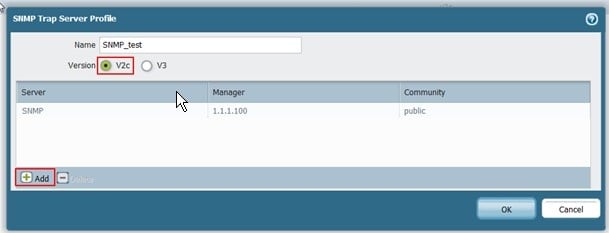
- Enable SNMP on your Palo Alto firewall (Device > Setup > Operations > SNMP Setup)
- Configure community strings or SNMP v3 credentials
- Add the firewall as a device in PRTG using the IP address
- Use auto-discovery to create relevant SNMP sensors
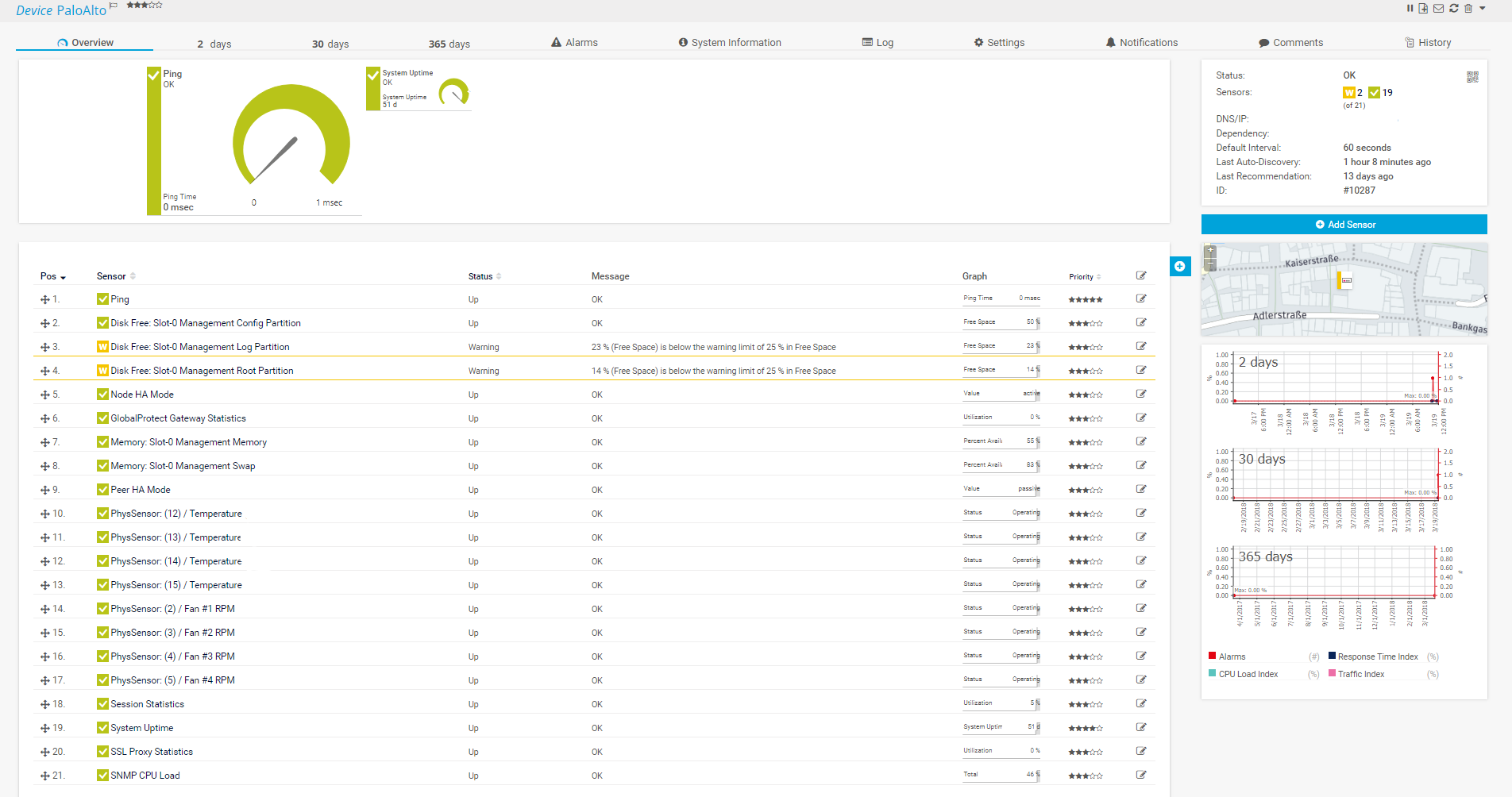
SNMP support allows you as the PRTG administrator to capture metrics about the following aspects of your device.
- CPU Usage
- Disk Usage
- Memory Usage
- Temperature
- Fan Status
- Node HA Mode
- Peer HA Mode
- Gateway Statistics
- Session Statistics
- SSL Proxy Statistics
XML API Monitoring for Advanced Metrics
For comprehensive monitoring beyond SNMP capabilities, PRTG can utilize Palo Alto's XML API. This method provides access to:
- Detailed threat log information
- Active session statistics
- VPN tunnel status and throughput
- Configuration commit status
- High availability (HA) pair status
Syslog and NetFlow Integration
Palo Alto firewalls can forward syslog messages and NetFlow v9 data to PRTG:
Syslog monitoring captures security events, system alerts, and configuration changes. Configure your Palo Alto firewall to send syslog messages to PRTG's IP address on port 514.
NetFlow monitoring provides detailed traffic analysis and bandwidth utilization insights. Enable NetFlow export on your firewall interfaces to capture comprehensive traffic patterns.
How Do I Configure SNMP on My Palo Alto?
For details on how to configure SNMPv2 on the Palo Alto Networks firewall, please see this article.
I Don't Have Time to Play with MIBs!
We understand, and we've done the heavy lifting to make monitoring your Palo Alto painless. Thanks to our wonderful developers and tech support team, we have a growing collection of device templates with all the settings needed for you to monitor your Palo Alto. You can find the detailed instructions for implementing this device template here.
The device template creates available and compatible sensors based on the data available. The sensors implement default alerts whenever possible, but you can still fine-tune most channels by defining additional limits in the sensor channel settings or by modifying the lookups that are included by default. There is no MIB importer, no library sensors, and no trial and error. Along with out-of-the-box sensors for Ping, System Uptime, and Interface Traffic, you can now have a comprehensive view of your Palo Alto device within minutes.
PRTG supports monitoring Palo Alto firewalls through multiple protocols including SNMP v2c/v3, XML API integration, syslog message collection, and NetFlow v9 traffic analysis. The platform includes specialized sensors for VPN connection monitoring and can track over 100 different firewall metrics simultaneously.
Palo Alto Sensors
In the image below you can find a monitoring overview of Palo Alto sensors.
How Do I See Bandwidth Consumption?
When you identify spikes and upward trends on your interfaces (SNMP Traffic) you will need Netflow for aggregate bandwidth monitoring. This can be setup quickly and easily on your device and forwarded to PRTG for analysis within a Netflow sensor.
REST API Anyone?
One of our PRTG users wrote a PowerShell script for monitoring an IPSec VPN Tunnel via the rest API on a Palo Alto.
This is just another example of the customization and flexibility of PRTG to capture and monitor devices and services in countless ways. IT professionals need to collect as much data from their environment as possible to ensure everything is working properly.
Why Choose PRTG for Palo Alto Monitoring?
Unlike single-protocol monitoring solutions, PRTG's multi-protocol approach ensures no blind spots in your firewall monitoring. While other tools focus solely on log analysis or SNMP data, PRTG correlates information from SNMP sensors, syslog events, NetFlow data, and API calls to provide complete visibility into your Palo Alto firewall infrastructure.
Helpful Links and Resources
For all those who want more information, here is a list of further resources:
- How to Configure SNMPv2 on the Palo Alto Networks Firewall
- PRTG Device Templates on GitLab
- Palo Alto Device Templates on GitLab
- Paessler Knowledge Base - How can I monitor Palo Alto firewalls with PRTG?
- How to setup NetFlow on Palo Alto firewalls
- Hospitable IT - Monitoring an IPSec Tunnel on a Palo Alto Firewall Using PRTG
👉 Ready to monitor your Palo Alto firewall infrastructure? Download your free PRTG trial and start monitoring in minutes. Test all monitoring methods and receive expert setup guidance.
 Published by
Published by