After the OpenSSL Heartbleed bug and the SSL 3.0 POODLE vulnerability another encryption attack has emerged that enables exploiters to read and modify data passing through encrypted connections.
Possible attackers might use this new vulnerability, called Logjam, to downgrade encrypted connections between a user and a web or mail server to 512-bit cryptography, which is weaker and can more easily be decrypted.
Since version 14.4.12 (released in October 2014) PRTG Network Monitor is safe. We use unique pre-generated Diffie-Hellman (DH) parameters, which use a 1024-bit key as a default. If you're interested in how you can generate a DH key that is longer than the existing default key in PRTG, please have a look at this Knowledge Base article on "Modifying Key Length for Diffie-Hellman Parameters".
You can test the security of your PRTG server at weakdh.org—if your PRTG installation is up-to-date, you will receive a similar result as the following:
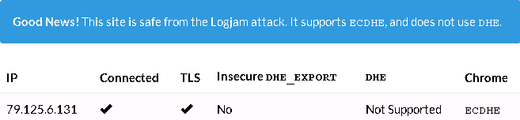
If you are using a PRTG version older than 14.4.12, please update to the newest PRTG stable release:
- Freeware/PRTG 100/Trial users: Just go to Setup | Auto Update in the main menu and update your installation for free;
- Updating Commercial Licenses is just as easy: Please go to Setup | Auto Update in the main menu to update your installation. This update requires an active maintenance contract. Log in on our customer service portal to check if you still have active maintenance or if you need to renew your maintenance. When in doubt please contact sales@paessler.com for assistance.
 Published by
Published by 











