You no doubt know the OSI model, and you probably work with it every day. If you're a sysadmin and don't know what I'm talking about, then... no, everyone knows what I am talking about! 😊
Network monitoring must deal with all layers of communication between humans. This is in addition to the classic seven. The difference being that this one is less technical and therefore harder to measure or quantify. But also that, strangely enough, the problems it causes are often the most unpredictable. A network is not just made up of switches, cables, applications and security software. If not of this physical level, it is composed of a vital component in the smooth functioning of your network. We're talking about the human factor, a layer we like to call Layer 8.
The original OSI model consists of seven abstraction layers, starting with the physical layer right up to the application layer. Where was the presentation layer again? And which networking committee defined the layer?
If you want to refresh your knowledge before you read on, let's have a look at the definition and the overview of the layers.
The OSI (Open Systems Interconnection) model was created by the ISO to help standardize communication between computer systems. It divides communications into seven different layers, which each include multiple hardware standards, protocols, or other types of services.
The OSI model consists of the following layers:
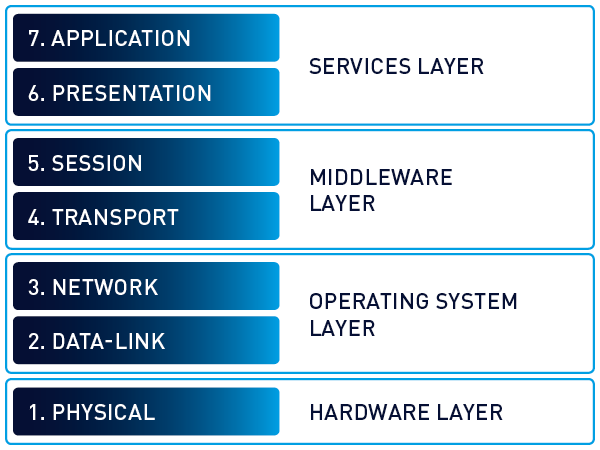
So now we all remember how the OSI model is structured and know where layers like the transport layer, the network layer or the session layer are .
In addition to the traditional, seven-layer OSI model, you also hear about the so-called "Layer 8". Admins like to use the term "layer 8 issue" when it comes to errors caused by a user. These are mostly users who do not master the handling of IT technology well enough from the admins' point of view and who make avoidable mistakes.
Understanding Layer 8 in the extended OSI model
But there is also another, more serious definition of Layer 8.
Bruce Schneier and the company RSA Security LLC invented the concept of layers above the OSI layer.
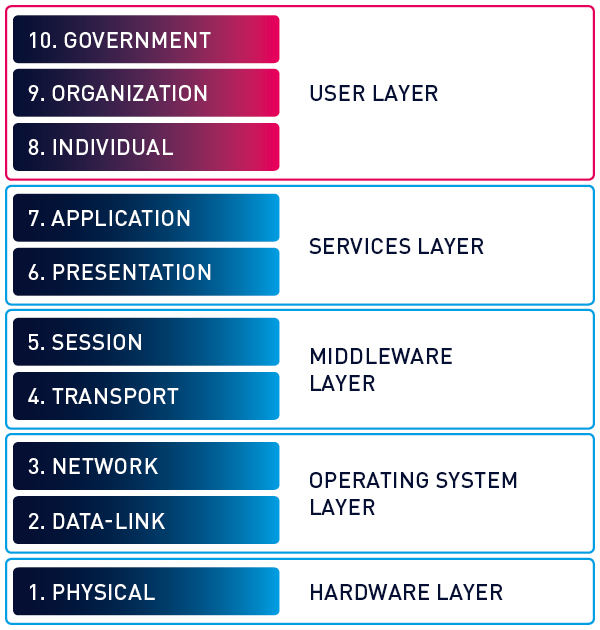
iSide note: Layer 0 is often referred to as the cabling infrastructure which is almost everything that the physical layer, Layer 1, needs to exist at all. If you want to delve a little deeper, you can find more information here.
During troubleshooting, the user layer is both the most complex and often the most opaque. Whenever a problem cannot be explained logically, even after several views, you should take a closer look at the user layer! It may well be that it is a code 18!
Layer 8 monitoring: Preventing user-related network issues
Well, in the first step, and this is very important, we have to distinguish between monitoring and surveillance.
In the context of this article, I will not go into the possibility of physically monitoring employees in any form, neither in the form of video surveillance, nor any other surveillance of the workplace.
I am much more concerned with scenarios in which users interact with systems and in which these actions need to happen within a defined framework.
Layer 8 monitoring use cases: Protecting against human error
In the end, any kind of social engineering, SPAM, scam, phishing or online fraud is a conceivable use case.
- Employees who find a prepared USB stick in the company car park and plug it into the USB slot of a company computer.
- Users who receive a telephone call where the other person pretends to be their boss and advises an urgent bank transfer.
- The careless handling of classic phishing emails that contain links to malicious websites or even malicious code as attachments.
You can't monitor which links your users click, but you can at least check if the antivirus solution is up-to-date on all devices and if the software firewall is active. Our PRTG WMI Security Center Sensor, for example, can be of assistance here.
In addition to this, you always have to reckon with inconsiderate actions on the part of your users. How easily is a folder in the file system accidentally deleted or the contents of a database file destroyed? To always have an eye on this, take a look at our different PRTG File Sensors like PRTG File Sensor, WMI File Sensor, File Content Sensor, or Folder Sensor.
Impatient users also tend to turn off computers during a logon or logoff process that they feel takes too long. The fact that updates to the system or an application are carried out in the background is not visible at this moment. Often this impatience leads to a computer that does not start anymore or that does not run stably.
To counter this, you can monitor the unexpected shutdowns of the devices of such impatient colleagues. Just use our PRTG Event Log (Windows API) Sensor in this case.
Since the success of the series The IT Crowd, every admin knows the often-quoted sentence, "Have you tried turning it off and on again?". I don't know how many times during my time in IT support users credibly assured me that they had already restarted the computer several times. A look at the system uptime of the computer brought the truth to light! With PRTG you can monitor system uptime based on WMI (PRTG Windows System Uptime Sensor) as well as SNMP (PRTG SNMP System Uptime Sensor).
Effective Layer 8 Monitoring with PRTG Network Monitor
While we can't directly monitor human behavior, PRTG Network Monitor provides several powerful tools to help mitigate Layer 8 risks:
Security Monitoring
PRTG's WMI Security Center Sensor ensures your users' devices maintain proper security protocols by verifying that antivirus solutions are up-to-date and software firewalls are active. This creates a protective layer against phishing attempts and malware that might exploit user error.
File Integrity Monitoring
Accidental file deletions or modifications are common Layer 8 issues. PRTG's comprehensive file monitoring sensors (File Sensor, WMI File Sensor, File Content Sensor, and Folder Sensor) help you track critical files and folders, alerting you to unexpected changes before they cause significant problems.
System Behavior Analysis
The PRTG Event Log (Windows API) Sensor can detect patterns that suggest user-related issues, such as unexpected shutdowns during updates. Similarly, PRTG's System Uptime sensors (both WMI and SNMP versions) can verify system uptime claims and identify devices that experience frequent reboots, often a sign of user impatience or improper handling.
Comprehensive Visibility
With PRTG's customizable dashboards, you can create a holistic view of your network that helps identify anomalies potentially caused by Layer 8 issues, allowing for faster troubleshooting and resolution.
As you can see, even though it might not be easy to keep an eye on Layer 8 directly, PRTG Network Monitor offers all the tools you need to identify and remediate the effects of issues related to the human element on your IT environment. You just need to find the right balance.
In the case of Layer 8, the best prevention method is still regular user awareness training. This, of course, should be backed by active monitoring of the systems that can affect or be affected by people’s actions with the technology they work with. PRTG Network Monitor is ideal to offer you the necessary visibility over your entire IT infrastructure.
Do you want to take a proactive approach to Layer 8? Download PRTG Network Monitor now and see how our all-in-one monitoring solution can help you secure your network from technical as well as non-technical factors.
 Published by
Published by 




.jpg)