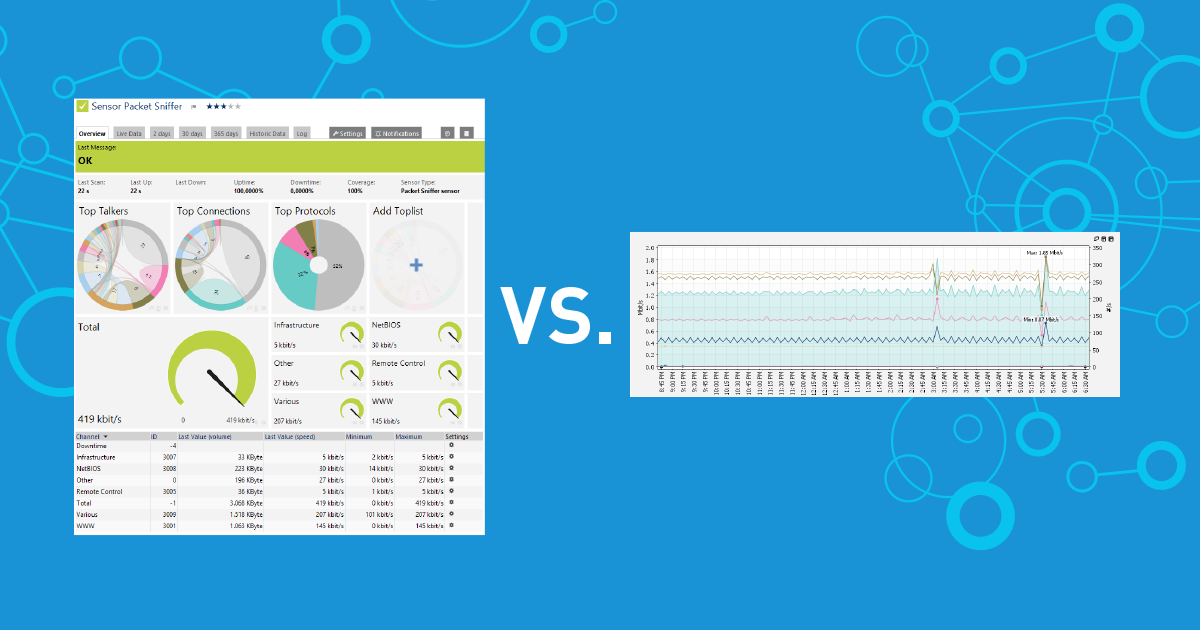
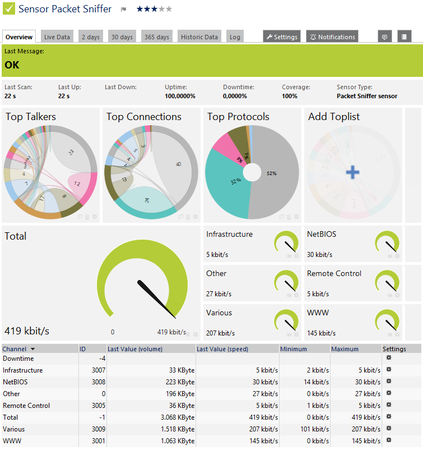
Flow based monitoring (NetFlow, sFlow, jFlow, IPFIX...) is a powerful method to get detailed information about the traffic on your switches and firewalls. It not only delivers data about the sheer amount of traffic, but also what kind of traffic it is, where it comes from and where it goes to. Using flow monitoring you can get top lists of users, connections or protocols.
However, not every switch, router, or firewall supports flow protocols. Most flow protocol supporting devices are expensive high-end series, while older devices or budget series don't support it. You can find more information about flow monitoring at the Paessler manual.
1. Basic Traffic Monitoring Via SNMP
SNMP (Simple Network Management Protocol) is a basic protocol supported by most devices, from switches to router, firewalls, servers, and sometimes even coffee machines. Vendors of SNMP supporting devices usually offer MIB (Management Information Base) files for their devices which enable the user to create individual OID (Object Identifier) libraries to request the required information from his device. For details about SNMP, MIBs, or OIDs check our knowledge base.
Paessler offers a free tool for download, the Paessler MIB Importer and Converter, that helps creating custom OIDs from MIBs:
However, SNMP only delivers basic traffic information, it's just about traffic in/out per interface. It can't tell you what kind of traffic, where it comes from and where it goes to. No lists of top talkers, protocols or users. But there is another option, that can do:
2. Advanced Traffic Monitoring Via Packet Sniffing
Like Flow monitoring, packet sniffing reads information about traffic from the data packets' headers. To do so, your switch must support port mirroring, also called port monitoring or SPAN (Switch Port Analyser). If it does, you must connect the mirror port of your switch to a computer running a PRTG probe on. This Windows based PC must have 2 network cards then. One connected to the mirror port, and a second one connected to a "normal" switch port, as often mirror ports just copy traffic, but does not switch/route normal traffic (so the Probe PC wouldn't be able to communicate back to the PRTG Core Server, it would only receive the mirrored traffic).
Another option is to send the traffic you want to monitor through a device you're running a PRTG probe on. Choosing this option, you must be aware that you're creating a bottleneck for your network traffic. So, this would be a viable method if it's only about a limited amount of traffic.
At the PRTG manual you can find a step-by-step guide about how to set up the PRTG Packet Sniffer Sensor.
You can also find some more details about sniffing and how it works.
 Published by
Published by